- Details
-
Published: Monday, 13 May 2019 15:07
-
Written by Riccardo Gallazzi
WordPress released 5.1.1
WordPress 5.1.1 is now available; this is a Security Release that does not introduce new particular functions but focuses on solving security problems and improving the current system.
In particular it proposes 14 improvements and bugfixes (available here), including functions to facilitate the transition to the minimum version of PHP that will be requested by WordPress 5.2 (released in late April) and a sanitization of the comments stored in the database in order to prevent Cross-Site Scripting attacks.
Joomla 3.9.4 is available
Joomla has released version 3.9.4 of the popular CMS.
Version 3.9.4 is a security release that does not introduce functional innovations but a system of problems. Among the improvements of this version we report the remediation of 3 Cross-Site Scripting (XSS) vulnerabilities, the addition of plugins for Terms of Use and Privacy Consent, functions tracked for User Action Logs, adding subtitles to featured articles.
More details are available in this Joomla blog post.
Read more ...
- Details
-
Published: Tuesday, 07 May 2019 16:08
-
Written by Lorenzo Bedin
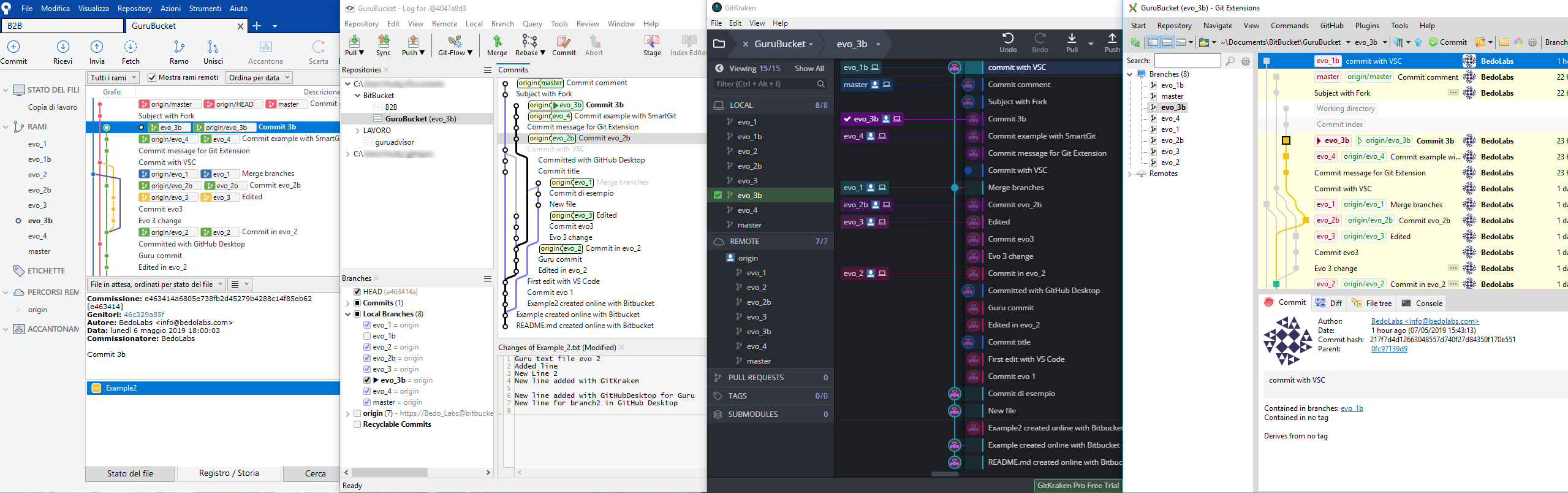
In the last two issues of GURU advisor we covered advantages and use cases of Git. An important aspect to take the best out of this technology is the choice of the client to use.
So we’ve decided to test a selection of Git clients with a graphical interface by trying a typical sequence of operations, always the same one, to simulate a typical use experience.
Selection and Procedure
There are plenty of Git clients, but our selection covers eight of them; such a wide assortment indicates a certain attention from the development world on this tool, which cover anything between important projects like GitKraken and simplified tools like TortoiseGit.
Apart from UnGit which is Web-based, the remaining tools are available on both Windows and Mac, while Linux support is not offered by all of them.
The sequence of operations we just talked about is pretty basic, yet it coverS every fundamental operation that can be done with these tools, regardless of advanced capabilities that, however, many of these tools support. The first phase is cloning a repository, followed by an overview of the dashboard, then adding a branch and commit it.
Read more ...
- Details
-
Published: Thursday, 02 May 2019 16:32
-
Written by Guru Advisor
Intro article -> An introduction to GitLab
GitLab’s homepage is as follows, with a toolbar in the upper part and an activity box on the left (referred to the actual repository) with access to branches. Clicking Commits shows the related chronology in addition to the state of branches with the homonymous section. The commit feature is used to individuate users and activities on files (addition, modification, deletion).
GitLab: creating a repository
You must register at gitlab.com and create an account in order to use GitLab; then you’ll be redirected to the main projects page, which can be reached by the Projects item in the toolbar. The best way to start a project is to create a group to define users, permissions and repos, then hit Create a Project.
This is when you can decide wether to start a project from scratch, from a template or to import it. In the Visibility Level section you can define the access to the project: private, internal (whoever is logged in gitlab.com) or public. The latter is the case where anybody can partecipate in, while Internal is the ideal solution when GitLab in installed on an on-premises platform.
The main management window has the commands to start working with a plain project.
Read more ...
- Details
-
Published: Wednesday, 01 May 2019 16:32
-
Written by Guru Advisor
Previous article: intro to Ansible
Here we are with our journey in the Ansible world, this time we’ll look at the other fundamental features of its structure and use.
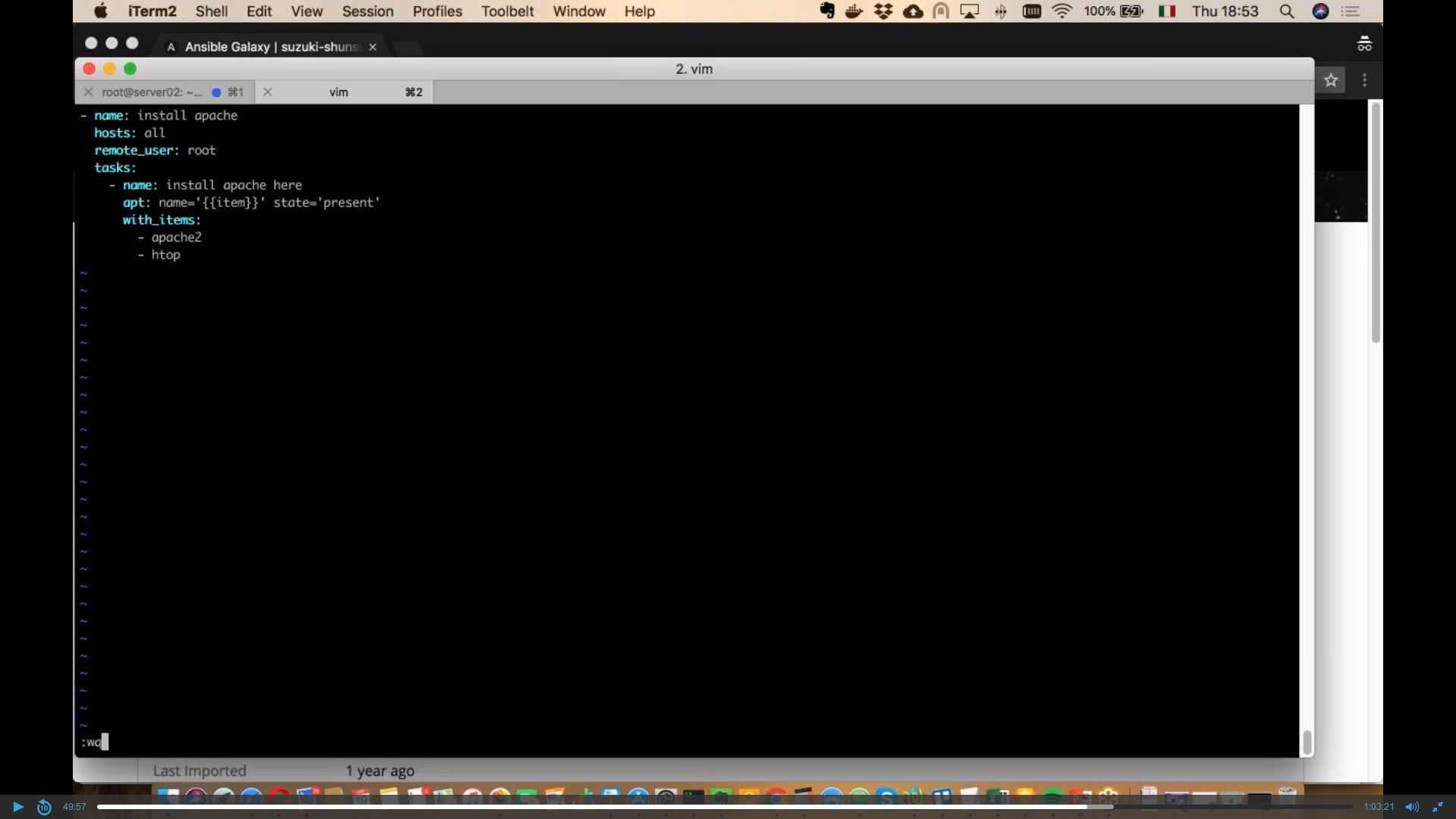
Play and playbook: what is the difference?
An example of playbook is portrayed in the image below, which shows the content of a YAML file which constitutes the playbook itself. This particular one actually contains a single play: this is the limit-case where play and playbook are the same thing.
The play contains two tasks with the definition of the destination hosts (host: web), the become command (with the -yes parameter stating that hosts become so after the installation) and the variables the we want to define with the -var parameter.
Read more ...
- Details
-
Published: Thursday, 13 December 2018 15:47
-
Written by Veronica Morlacchi
La data protection by design è uno dei criteri fondamentali indicati dall’ormai noto GDPR che un titolare di un trattamento di dati personali deve rispettare, sia al momento di determinare i mezzi di quel trattamento sia all’atto del trattamento stesso, nell’adempimento del suo dovere di responsabilizzazione (“accountability”). Anche la tecnologia deve essere progettata per operare nel rispetto della privacy by design, e, dunque, nel rispetto dei diritti fondamentali delle persone fisiche i cui dati vengono trattati.
La c.d. privacy by design, ovvero, protezione dei dati fin dalla progettazione, è uno dei capisaldi del GDPR e fa riferimento all’approccio da utilizzare, nel momento in cui viene pensato un trattamento di dati personali e prima ancora che venga iniziato, ovvero alle modalità tecniche ed organizzative da adottare nell’organizzazione di quel trattamento di “dati personali” - che, si ricorda incidentalmente, sono definiti ex art.4, n.1 come “qualsiasi informazione riguardante una persona fisica identificata o identificabile («interessato»)”.
Read more ...
- Details
-
Published: Thursday, 13 December 2018 15:47
-
Written by Guru Advisor
Software development doesn’t include the knowledge of programming languages, debug techniques and how to optimize the code only, it also deals with a proper and coherent management of the different versions of the same code: versioning.
Be it the work of a single developer or of a team distributed on different geographic areas, versioning is an essential aspect of software development, due to large codebases to manage as well. In order to face the challenge, several platform were designed, with Git standing on top: Git is a versioning engine that can be managed via CLI or graphical interface, locally or via Web.
Git is also at the basis of many products/services, with GitHub and BitBucket being the most used.

In this article we are going to get acquainted with Git by leveraging Gitlab as a testing environment to discover its fundamental aspects: what is Git and how it works, what commits, repositories and branches are, and the main differences between on-premises and Cloud versions.
Read more ...
- Details
-
Published: Wednesday, 28 November 2018 16:54
-
Written by Lorenzo Bedin
We at GURUadvisor we’ve often talked about FreeNAS as a strong and evaluated open-source platform for the realization of NAS systems (even with non-dedicated hardware). We’ll now analyze an interesting alternative, open-source too, by discovering key features and weaknesses.
Openmediavault -or OMV for the sake of brevity, is a Debian based operating system, optimized and customized for the implementation of Network Attached Storage solutions: its main field of use is in labs, homes and SMBs. The main features include the support to the main network services (SSH, FTP, SMB/CIFS, Rsync and so forth), logic volumes management, S.M.A.R.T. checks on disks, email notifications, link aggregation and plugins to further expand its features.
Read more ...
- Details
-
Published: Wednesday, 31 October 2018 16:09
-
Written by Guru Advisor
Ansible is an open source software conceived to help sysadmins to manage the automation and a centralized orchestration of configuration procedures on Unix-like architectures. Its main characteristic is a mix of richness in features and an easy learning curve.
Ansible leverages two structured elements: node and control machines. As the name suggests, the latter are the computers that actually realize orchestration by means of commands for the underlying nodes via SSH and JSON. A very important point of strength of Ansible is being comprehensible without particular development skills (a prior knowledge of syntax and constructs is not required), tied with a sequential execution of control tasks.
Its main uses are application deployment, distributed configuration management and work fluxes orchestration.
Read more ...
- Details
-
Published: Friday, 20 July 2018 12:24
-
Written by Lorenzo Bedin
WordPress 4.9.7 is now available
WordPress has released version 4.9.7.
Being a "security and maintenance release", no new significant functions are introduced, rather some critical issues and problems are fixed, among which:
- Fixed library bug that allows a user with certain permissions to delete files out of the media folder
- Taxonomy: improved cache management for queries
- Post and type of post: on logout, deleted cookie password
- Widget: basic html tag in the description in sidebar
- Community events Dashboard: Always show the nearest WordCamp
- Privacy: the default content of the privacy policy no longer causes an error when you delete the rewrite rules
Read more ...
- Details
-
Published: Friday, 20 July 2018 12:15
-
Written by Lorenzo Bedin
It has been just a few issues when we described the Technical Preview release of Windows Server 2016, and here we are talking about Microsoft’s next server operating system.
Windows Server 2019 maintains the solid basis of the previous release, which is Microsoft’s server OS whose diffusion has been the fastest, whose release is expected in the second semester of this year. It will be an LTSC edition (Long Term Servicing Channel), so the distribution channel will have a release update every 2/3 years, unlike the typical SAC model (ie Windows 10).
The key points of the development are four, and they come from the analysis of future trends and requests received by Microsoft from clients’ feedback channels: security, hybrid Cloud, application platforms and hyper-convergent environments.
Microsoft naturally worked a lot on the first of these aspects in order to offer a system that can face and resist to the ever growing number of threats. The security approach is based on three specific macro-areas: Protection, Identification and Response. In terms of protection, now Linux VMs can leverage Shielded VMs (introduced in Windows Server 2016), thus being protected against illicit and undesired activities. Add to that the introduction of Encrypted Networks, which will allow sysadmins to encrypt data traffic on whole network segments thus protecting the communication between nodes.
Read more ...
- Details
-
Published: Thursday, 05 July 2018 10:25
-
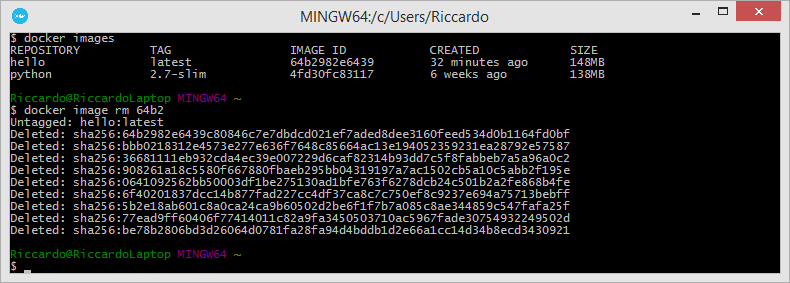
Written by Riccardo Gallazzi
Previous article -> An introduction to Docker pt.2
The Docker introduction series continues with a new article dedicated to two fundamental elements of a containers ecosystem: volumes and connectivity.
That is, how to let two containers communicate with each others and how to manage data on a certain folder on the host.
Storage: volumes and bind-mounts
Files created within a container are stored on a layer that can be written by the container itself with some significant consequences:
- data don’t survive a reboot or the destruction of the container.
- data can hardly be brought outside the container if used by processes.
- the aforementioned layer is strictly tied to the host where the container runs, and it can’t be moved between hosts.
- this layer requires a dedicated driver which as an impact on performances.
Docker addresses these problems by allowing containers to perform I/O operations directly on the host with volumes and bind-mounts.
Read more ...
- Details
-
Published: Thursday, 12 April 2018 18:00
-
Written by Riccardo Gallazzi
PrestaShop 1.7.3 is now available
PrestaShop announces the new 1.7.3 version, which includes improvements and new features.
Among the new features introduced we find:
- PrestaTrust, a function which authenticates the code of the modules with PrestaTrust support and records the license information in the block-chain.
- Right-to-left support: support for right-to-left languages (RTL) is added, such as Arabic, Hebrew, and Persian.
A new set of demo products
- UI kit for modules, core and back-end, with support for Bootstrap 4 jQuery 3.
- Symfony: three new pages have been migrated to the popular PHP framework
- Other features and improvements, such as setting delivery times, sending alerts when a product reaches low availability in stock, bulk actions in the stock, added localization in Icelandic and installation wizard in Japanese.
PrestaShop 1.7.3 is available at this address.
Read more ...
- Details
-
Published: Wednesday, 11 April 2018 14:29
-
Written by Riccardo Gallazzi
Previous article -> Introduction to Docker - pt.1
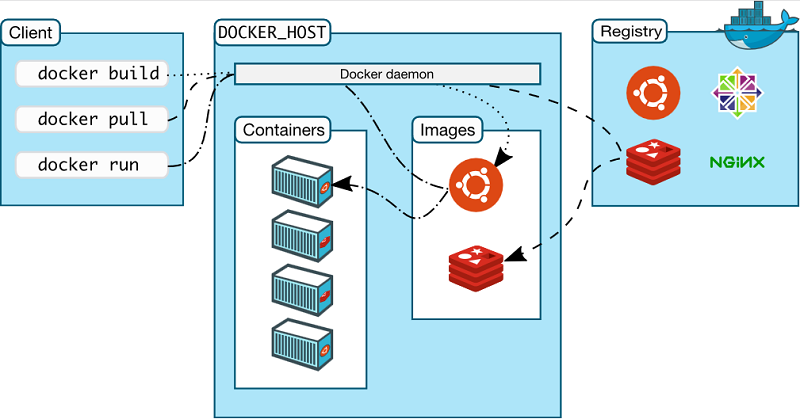
Images and Containers
An image is an ordered set of root filesystem updates and related execution parameters to be used in a container runtime; it has no state and is immutable.
A typical image has a limited size, doesn’t require any external dependency and includes all runtimes, libraries, environmental variables, configuration files, scripts and everything needed to run the application.
A container is the runtime instance of an image, that is, what the image actually is in memory when is run. Generally a container is completely independent from the underlying host, but an access to files and networks can be set in order to permit a communication with other containers or the host.
Conceptually, an image is the general idea, a container is the actual realization of that idea. One of the points of strength of Docker is the capability of creating minimal, light and complete images that can be ported on different operating systems and platforms: the execution of the related container will always be feasible and possible thus avoiding any problem related to the compatibility of packages, dependencies, libraries, and so forth. What the container needs is already included in the image, and the image is always portable indeed.
Read more ...
- Details
-
Published: Wednesday, 11 April 2018 11:38
-
Written by Lorenzo Bedin
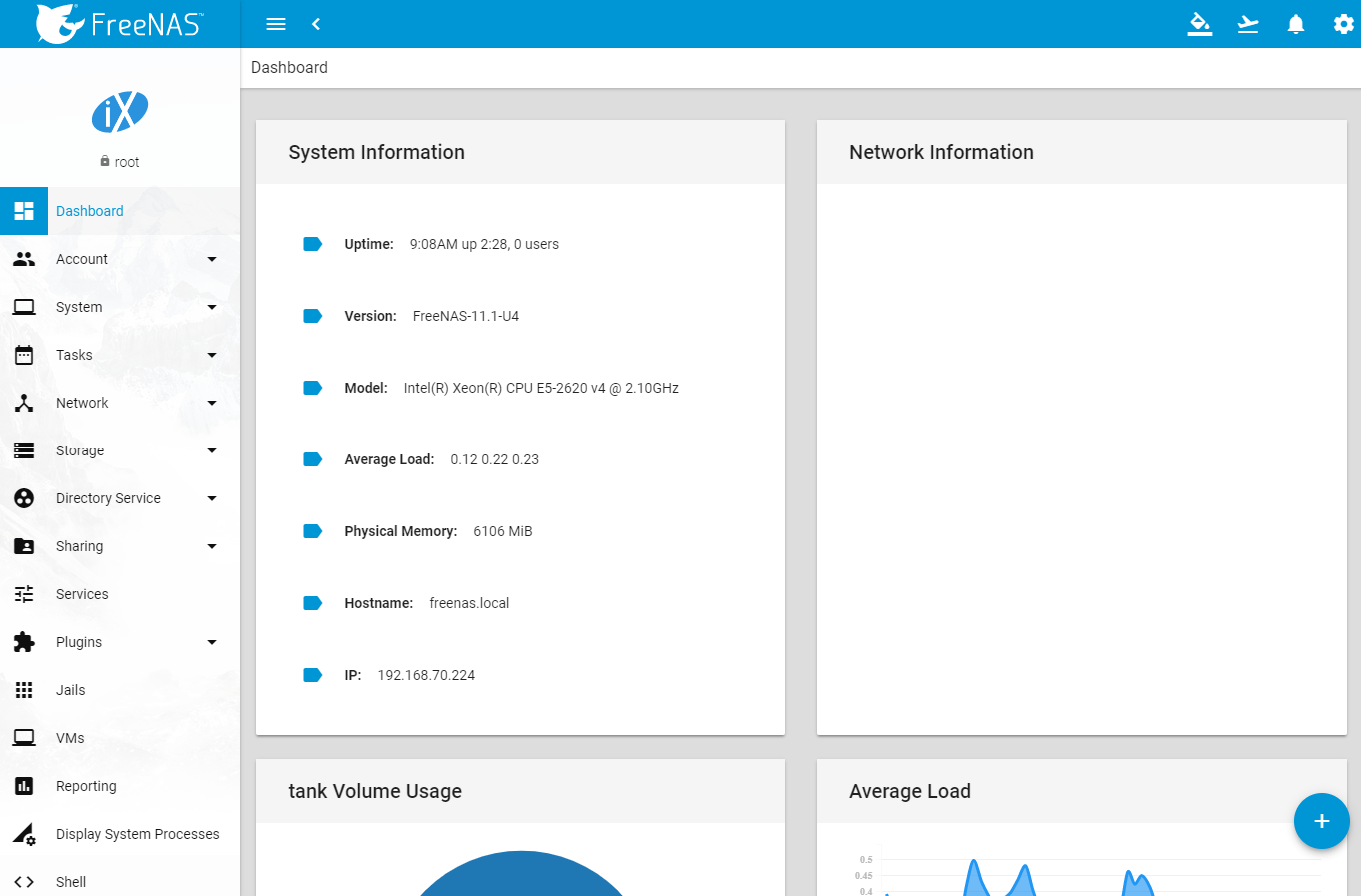
A few months ago we talked about the troubled release of the last two FreeNAS versions, which involved a new graphical interface, the premature dismissal of Corral and finally the development of the 11.0 version with the return of the classic UI.
But IXSystems didn’t discourage and kept on developing its NAS system and eventually released the all-new 11.1 version.
Not just a new appearance, but also new features
Let’s start with the aspect that usually draws most of the attention of a system, otherwise quite traditional in terms of features: the new graphic interface.
The dark and edgy theme portrayed in a previous review, developers chose a more comfortable theme based on light colours with a tidier and neatter graphical organization. The overall design resembles the one on latests generations Android systems, quite flat and with icons and volumes characterized by circular contours and vivid colours.
The upper horizontal menu finally disappears, replaced by a lateral float-out unit which contains the usual features. The organization of voices has been revised and rearranged too, still being coherent with the classic one we’re used to. Another new feature of the UI is a proper visualization on mobile devices too, something the previous releases didn’t accomplish well.
Read more ...
- Details
-
Published: Monday, 29 January 2018 12:21
-
Written by Riccardo Gallazzi
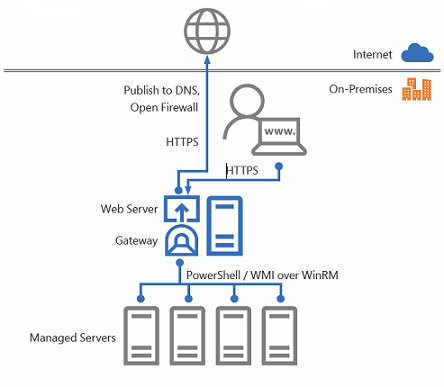
Announced last 14th September with a TechNet blog post, Project Honolulu is the free, Web-based HTML5 platform for centralized management of hosts and clusters that allows to control, manage and troubleshoot Windows Server environments from a single panel. Today is available as a “technical preview”.
Typically, the administration Windows server environments relies upon MMC (Microsoft Management Console) and other graphic tools, in addition to PowerShell, which guarantees a powerful and complete scripting system capable of an high level of automation.
Project Honolulu can be compared to VMware vCenter’s Web Client (albeit some differences), is a centralized management solution for Windows Server hosts and clusters, conceived not as a replacement for System Center and the Operations Management Suite, but as a complementary tool.
Projet Honolulu is the natural evolution of Server Management Tools (SMT is the analog tools retired a few months ago because as it ran on Azure, it required a constant Internet connection that sometimes it can’t be guaranteed) and represents its local, on-prem version. It’s not a substitute for MMC.
During last Ignite, Microsoft introduced the project with two demo sessions (one and the other), and covered the topic with a blog post.
Read more ...
- Details
-
Published: Monday, 29 January 2018 12:21
-
Written by Lorenzo Bedin
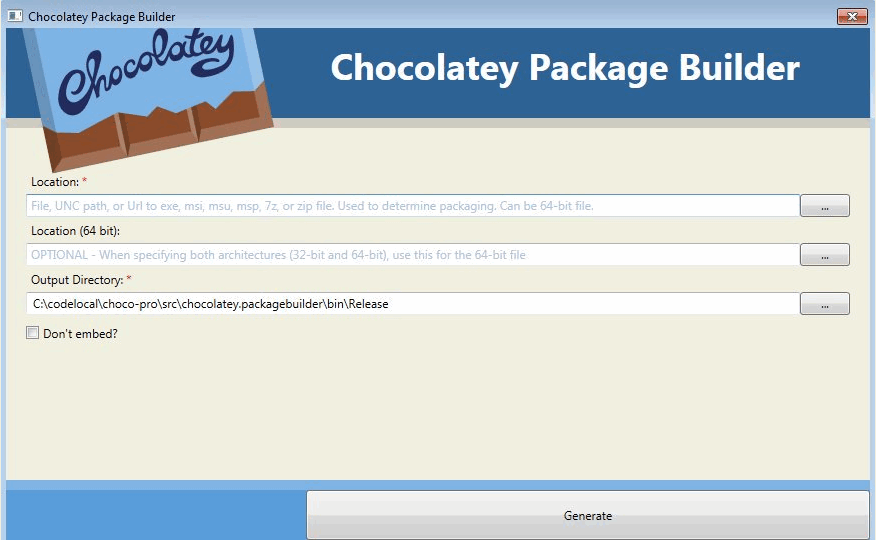
Chocolatey is a package manager similar to Linux apt and yum to create, update, distribute and remove software packages in a centralized and automated manner.
Two are the platforms at its basis: NuGet and Windows PowerShell. The former is a .NET package manager on its turn, and the former is the well-known integrated shell of the Microsoft Windows world. Available both as a command line tool and with a GUI, Chocolatey is an open source project with three licensing models: free, Pro and Business, with the additional MSP and Architect plans for specific uses.
Read more ...
- Details
-
Published: Monday, 29 January 2018 12:21
-
Written by Riccardo Gallazzi
CMS
Joomla 3.8.3 is now available
Joomla 3.8.3 is now available; this is a security release that doesn’t introduce any new feature, rather it fixes security issues and improves performances.
In particular, this release adds support for PHP 7.2 multiple download sources on update servers (AKA download mirrors), TinyMCE has been updated to version 4.5.8, improvements for multilingual support and search performances for big sites. A complete list of fixes is available at this address.
This version is available within the admin console or at this address.
Meanwhile, the Alpha 1 version of the upcoming Joomla 4.0 is available. The preview include new Bootstrap 4 templates, removal of obsolete functions, a new installation wizards, integration of Joomla Framework packages and a renewed Application for Consoles.
WordPress 4.9 is now available
WordPress 4.9, nicknamed “Tipton”, is now available. This version introduces several new features, including a Customizer with new features, improvements to the system code, new widgets and several new features for developers like improved JavaScript API customizer, CodeMirror (a new library for code revision), MediaElement.js update to version 4.2.6 and other improvements to plugin and translation files management.
This version is available in the administration console or at this address.
Version 4.9.1 is available as well. This is a security release that doesn’t introduce any new feature, rather it fixes security issues. Improvements of this release include a properly generated hash for the newbloguser key instead of a determinate substring, addition of escaping to the language attributes used on html elements, ensuring the attributes of enclosures are correctly escaped in RSS and Atom feeds and removal of the ability to upload JavaScript files for users who do not have the unfiltered_html capability.
Eleven additional bugs have been fixed, including issues relating to the caching of theme template files, a MediaElement JavaScript error preventing users of certain languages from being able to upload media files and the inability to edit theme and plugin files on Windows based servers.
Further information about this version are available at this address.
Read more ...
- Details
-
Published: Monday, 29 January 2018 12:21
-
Written by Riccardo Gallazzi
You have heard about it for sure, it’s one of the hottest technologies of the moment and it’s gaining momentum quickly: the numbers illustrated at DockerConf 2017 are about 14 million Docker hosts, 900 thousands apps, 3300 project contributors, 170 thousands community members and 12 billion images downloaded.
In this series of articles we’d like to introduce the basic concepts in Docker, so to have solid basis before exploring the ample related ecosystem.
The Docker project was born as an internal dotCloud project, a PaaS company, and based on the LXC container runtime. It was introduced to the world in 2013 with an historic demo at PyCon, then released as an open-source project. The following year the support to LXC ceased as its development was slow and not at pace with Docker; Docker started to develop libcontainer (then runc), completely written in Go, with better performances and an improved security level and degree of isolation (between containers). Then it has been a crescendo of sponsorships, investments and general interest that elevated Docker to a de-facto standard.
It’s part of the Open Container Project Foundation, a foundation of the Linux Foundation that regulates the open standards of the container world and includes members like AT&T, AWS, DELL EMC, Cisco, IBM Intel and the likes.
Docker is based on a client-server architecture; the client communicates with the dockerd daemon which generates, runs and distributes containers. They can run on the same host or on different systems, in this case the client communicates with the daemon by means of REST APIs, Unix socket or network interface. A registry contains images; Docker Hub is a public Cloud registry, Docker Registry is a private, on-premises registry.
Read more ...
- Details
-
Published: Monday, 23 October 2017 11:44
-
Written by Riccardo Gallazzi
WordPress 4.8.2 is now available
WordPress release version 4.8.25.
This is a “Security and Maintenance Release” which introduces no new features, instead it fixes some security and performance issues of the most used CMS worldwide.
In particular these 9 problems are fixed, in addition to 6 performance fixes:
- $wpdb->prepare() can create unexpected and unsafe queries leading to potential SQL injection (SQLi). WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability.
- A cross-site scripting (XSS) vulnerability was discovered in the oEmbed discovery.
- A cross-site scripting (XSS) vulnerability was discovered in the visual editor.
- A path traversal vulnerability was discovered in the file unzipping code.
- A cross-site scripting (XSS) vulnerability was discovered in the plugin editor.
An open redirect was discovered on the user and term edit screens.
- A path traversal vulnerability was discovered in the customizer.
- A cross-site scripting (XSS) vulnerability was discovered in template names.
- A cross-site scripting (XSS) vulnerability was discovered in the link modal.
The update is available within the dashboard or at this address.
Who wants to preview the upcoming new release, can test WordPress 4.9 beta 3. Obviously it’s only for testing purposes and must not be installed in production environments.
Read more ...
- Details
-
Published: Monday, 23 October 2017 11:12
-
Written by Lorenzo Bedin
Emails are a powerful tool for businesses of all kind -Freelancers, Small and Medium Businesses and Big Corporates- to manage it in an efficient manner. In this article we will analyze email services offered by the main providers.
Emails are one of the main vectors of communication in the business world: they’re used for internal, informal, official and even international communications. Its use has, in several cases, ditched verbal communication and, because of that, each user expects this service to be quick, easy and -most of all- reliable. Beside sending and receiving messages, there’s a number of other activities that have merged together with them: calendars, address books, mobile synchronization, and so forth.
Read more ...
- Details
-
Published: Wednesday, 26 July 2017 15:06
-
Written by Roberto Beneduci
Properly keeping an IT infrastructure updated is a costly and weary activity: GFI’s LanGuard is a product conceived to structure and automate management process in a complete safety.
An example how dangerous is to have non updates systems is clearly shown by the very recent wave of infections by WannaCry, the ransomware that -albeit being targeted to a restricted number of users (they could have been way more had some remedies not been found promptly)- attacked Microsoft-based infrastructures in more than 150 countries. The ransomware exploited the EternalBlue vulnerability, which is available only on non-patched version of the operating system. Yet imagine what the outcome would have been if it targeted all Windows systems.
Read more ...
- Details
-
Published: Monday, 24 July 2017 11:21
-
Written by Riccardo Gallazzi
WordPress 4.8 is now available
WordPress 4.8 is now available, and this version introduces some new features: image, audio and video widgets, rich text widget for visual editing, improved link management and a new news section in the dashboard with all related WordPress events near you.
Further information are available in this post on the WordPress blog.
The update is available in the admin dashboard, we suggest to update as soon as possible but after doing a backup (just in case).
Joomla 3.7.3 is now available
Joomla has now reached version 3.7.3Joomla has now reached version 3.7.3, which is a minor release of version 3.x.
This release doesn’t introduce any new function, rather it fixes bugs and solves security issues.
In particular 2 XSS (Cross Site Scripting) and Information Disclosure vulnerabilities are fixed, which could pose a threat in terms of security.
The update is available directly within the admin dashboard.
Joomla 3.8 is expected at the end of July.
WordPress WP Statistics plugin is vulnerable to SQL Injection attacks
Suuri researchers discovered a vulnerabilitySuuri researchers discovered a vulnerability in the famous WP Statistics plugin for WordPress which permits SQL Injection attacks.
Version 12.0.9 of the plugin solves the issue, therefore we highly recommend to update the plugin as soon as possible.
Read more ...
- Details
-
Published: Monday, 24 July 2017 11:15
-
Written by Lorenzo Bedin
After a false start of the long awaited FreeNAS 10, the iXsystems development team a few weeks ago released the latest stable release of the operating system for NAS solutions.
We’ve extensively covered FreeNAS in previous issues by analyzing structure, functioning and advantages. We expect a high level of stability and reliability from such an operating system, yet we waited for almost a year the revolutionary release 10, code named Corral.
FreeNAS 10 “Corral”: something went wrong
The two main news would have been a new graphical interface and native support to multi-platform virtual machines.
However the release of Corral didn’t go as expected: after being available for 48 on the official FreeNAS website, it mysteriously disappeared and replaced by the previous 9.10 version. For some weeks nobody had a clue of what was going on, as it was still downloadable from the official repository; then it appeared in the Tech Preview section. A communicate was released on the FreeNAS forum on the 12th of April stating the motivations of the retirement of the release.
Read more ...
- Details
-
Published: Monday, 24 July 2017 10:51
-
Written by Riccardo Gallazzi
According to W3Techs, WordPress is used in 28,1% of the existing Internet websites, and it accounts for 59% of those based on a CMS (Content Management System), and the adoption rate is ever increasing. These numbers alore are enough to understand the great diffusion of WordPress: its easy installation and customization make it suitable to several use cases, eCommerce shop included.
But such popularity brings a downside: it’s one of the most attractive platforms to hackers. Luckily damages of an hacking attack can be prevented and limited with techniques and best practices that we will discuss in this article.
Read more ...
- Details
-
Published: Thursday, 08 June 2017 15:11
-
Written by Riccardo Gallazzi
WordPress 4.7.5 - Security and Maintenance Release is now available
While waiting for the release of version 4.8, expected in June, WordPress released version 4.7.5.
This is a “Security and Maintenance Release” which doesn’t add any new feature, it fixes security and performances issues.
In particular these 6 major problems have been fixed, in addition to other 4 fixes about performances:
- Insufficient redirect validation in the HTTP class. Reported by Ronni Skansing.
- Improper handling of post meta data values in the XML-RPC API. Reported by Sam Thomas.
- Lack of capability checks for post meta data in the XML-RPC API. Reported by Ben Bidner of the WordPress Security Team.
- A Cross Site Request Forgery (CSRF) vulnerability was discovered in the filesystem credentials dialog. Reported by Yorick Koster.
- A cross-site scripting (XSS) vulnerability was discovered when attempting to upload very large files. Reported by Ronni Skansing.
- A cross-site scripting (XSS) vulnerability was discovered related to the Customizer. Reported by Weston Ruter of the WordPress Security Team.
The update is available within the administration dashboard.
Read more ...
- Details
-
Published: Friday, 31 March 2017 17:22
-
Written by Riccardo Gallazzi
The new version of the most renowned backup tool for virtual environments adds the support to vSphere 6.5 and improves the integration with the Microsoft world with the support to Hyper-V and Active Directory.
Nakivo Backup & Replication is a backup and Disaster Recovery solution for virtual machines that offers on-site and off-site backup (with testing), replication, recovery (even single files and Exchange/Active Directory elements), Cloud replica (AWS) and multi-tenant capabilities. We have tried in advance for you the new 7.0 version. You can find our review of the previous release at this address.
Support to vSphere 6.5 and Hyper-V
The new version of vSphere came out a couple of months ago and all big players are updating the support to the new release, and Nakivo makes no exception: now you can add an ESXi 6.5 host or vCenter 6.5 to the Inventory and protect all VMs running there. The new support to Hyper-V (version 2012, 2012 R2 and 2016) is with no doubts the most exciting news of Nakivo Backup & Replication 7: the support is extended to virtual machines created and managed with the popular hypervisor by Microsoft. Now the product can cover both main virtualization platform available in on-premises and Cloud infrastructures, also supporting an hybrid solution with the capability of backing data up to the public cloud by Amazon: AWS EC2.
Read more ...
- Details
-
Published: Friday, 31 March 2017 17:22
-
Written by Lorenzo Bedin
In this article we have selected some of the new features available in Windows Server 2016 with the aim of analysing them and evaluating their impact in a real world scenario.
As we’ve mentioned in the previous issue, this new release is conceived as an improvement of the previous versions, rather than a brand new system. Ne features can be grouped into three ares: Virtualization and Containers, Security and Storage.
Virtualization
The main news in terms of Hyper-V is nested virtualization. With the new Windows Server 2016, Hyper-V hosts can be virtualized (ie a VM with Hyper-V running on it): this approach is often used in testing environments and situations where one wants to create multi-tenant environments without costs related to physical hardware. Now VMs’ hardware hot-add (disks, network cards, controllers, etc..) is supported: this operation was previously available upon powering off machines and restarting them with a subsequent downtime.
A new feature that is introduced with this version is the Host Guardian role, which we discussed in the previous issue. Host Guardian allows to regulate granularly levels and access permissions of Hyper-V administrators on virtual machines running on an host or cluster. Server 2016 also steps towards the Linux world: one of the main problems when creating a Linux VM was the lack of drivers certified for Secure Boot in Windows, which would lead to a “Failed Secure Boot Verification” error when starting the virtual machine; it could be solved by disabling the Secure Boot feature. This new release of Windows Server fixes the problem including such drivers.
Read more ...
- Details
-
Published: Friday, 31 March 2017 17:22
-
Written by Andrea Manzini
Xen, like VMware ESXi, is an hypervisor, that is, a software that allows to run several virtual machines -even with different operating systems, at the same time on the same hardware, sharing resources with the aim op optimizing costs and the management of the IT infrastructure. Given its nature, it’s often compared with concurrent platform by Microsoft (Hyper-V) and VMware (vSphere/ESXi), and in this article we are going to cover its characteristic.
A little bit of history
The Xen virtualization project was born in 2003 at the University of Cambridge as a research project. Within a few time XenSource was founded, before being acquired by Citrix in 2007, which keeps a free version but starts to develop a paid version. The project is backed by big players of the market like Intel, AMD, Cisco, Amazon, Google, Oracle, Samsung and Verizon.
In 2013 Xen became part of the Linux Foundation, and Citrix adopted an opensource licensing for its own XenServer product, then at version 6.2. The paid version, which included support and additional maintenance services, still remains.

Read more ...
- Details
-
Published: Friday, 31 March 2017 17:22
-
Written by Lorenzo Bedin
CentreStack is a managed server for the creation of an object storage platform that can be deployed between the walls and in Managed Service Provider mode to be offered as a service to clients.
The product of the american Gladinet is a system halfway between classic file servers for companies and off-premises Cloud storage platforms usually used in SaaS/PaaS mode (think of Dropbox, Onedrive, etc..). By taking the best from both worlds, CentreStack can leverage the internal IT infrastructure (servers, storage, etc..) to offer a file sharing service also suitable for BYOD purposes in a Cloud mode. Management indeed is completely Web based with a dashboard from where you can control and act on all aspects of the platform, be it multi-tenant and multi-node as well.

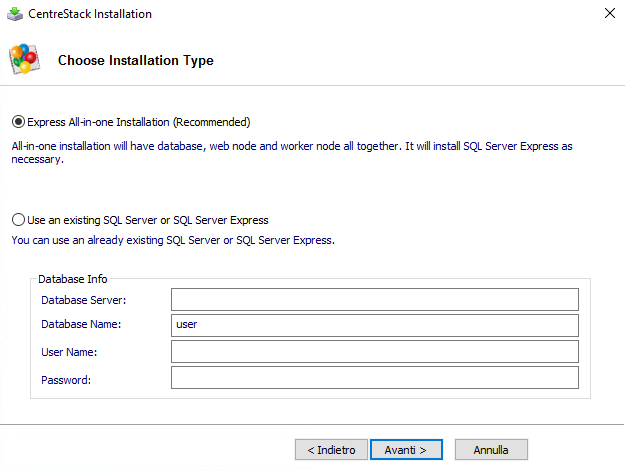
Structure and requirements
CentreStack is composed by three main parts, or nodes: Web Front Node, Worker Node and Database Node. Nodes can be deployed as physical hosts or as separate virtual machines, or in an all-in-one mode on a single host (a solution which is particularly suitable for small dimensions scenarios or testing purposes) where all components are installed at once. In some situations Web Front and Worker nodes can be condensed on a single machine.
Read more ...
- Details
-
Published: Tuesday, 24 January 2017 16:15
-
Written by Riccardo Gallazzi
WordPress 4.7.1 - Security and Maintenance Release is now available
Less than a month after the release of version 4.7 “Vaughan”, WordPress releases version 4.7.1 of the most used CMS in the world.
This is a “security and maintenance” release which fixes 8 important vulnerabilities that affect all WordPress versions (4. included), in addition to 2 bugs of the previous version.
The 8 vulnerabilities, which are now fixed, include cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks.
The update is available at the administration dashboard and at the official Website. We encourage you to update your installation as soon as possible.
Read more ...