Emails have become a key element in every business. In most cases the correspondence with clients and provides has such an importance that, in case of loss or theft, missing emails can result in heavy economical and organizational repercussions.
Securing email data is a crucial duty for every company. Emails can be protected by means of a traditional backup system or by an archiving system. A proper knowledge of both systems is required to avoid mistakes.
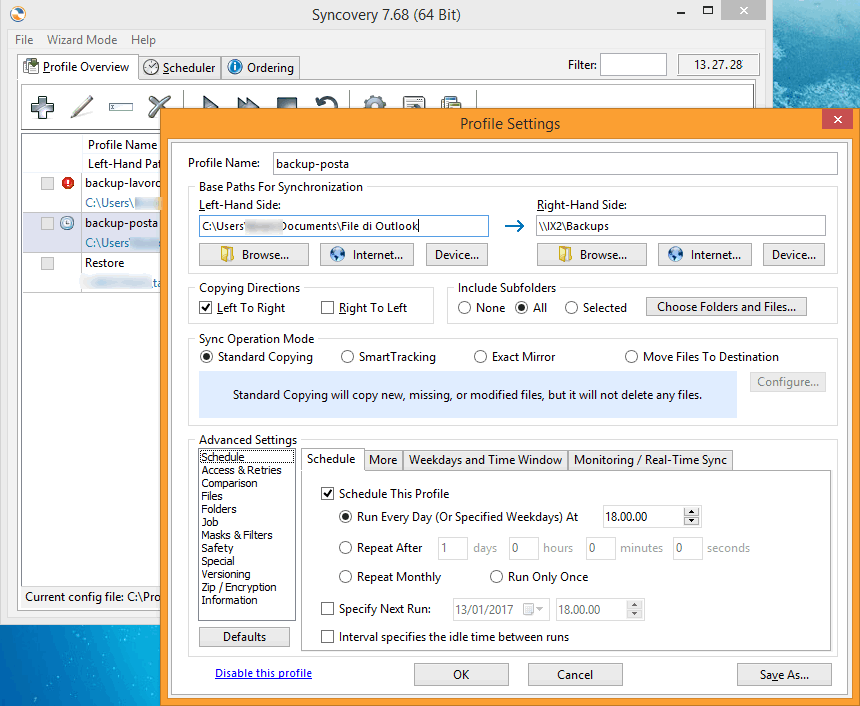
Backup is conceived as a “photography” (or a series of photos) of the system in a precise moment, for instance the saving of the email archive up to today. You can decide to keep one or more of such photos, maybe one each day for the last 5 working days. Retention describes the number of backup that are stored and its disposition in time (ie one backup per month for three months). A backup is created to retrieve messages deleted by accident or to restore a certain situation after software problems or any other issue that compromises the regular working process.
A good backup must have an easy restore routine and must store all necessary information: the position of the message in the folder structure and all its metadata (date, hour, sender, subject, etc..).
On the other hand, archiving is a process that aims to the long term (and possibly in read mode only) storage of the complete email archive. Archiving is not meant to be used for a restore in case of problems, but for data conservation (regardless of users behaviour). If, for instance, a user receives an offer and deletes it, such offer will be available within the archive and the company can retrieve it if needed. Archiving requires a bigger data space, especially if deletion is blocked, and often offers additional capabilities like full text indexing and quick research.
Naturally there are different and specific software and services for backups and archiving: they are, and must be, distinct and not interchangeable processes. This concept is somehow not immediate to understand, so let’s make some explanatory example to point out the aforementioned differences.
Case 1 - Brief term communications
A client sends you an email with additional information to an order. This email is clearly fundamental because, should the order be processed without taking these new considerations into account, the client might complain about it. As the order is still in progress, all exchanged information is recent; in this case, which is limited to a few days timespan, the lack of such email can be easily identified.
Case 2 - Emails disappear
One day you fire up your email client and notice that all emails are gone, just like it were deleted on purpose or as a mistake. We all experienced this circumstance at least once: seeing your own mailbox completely blank is an awful experience. Both situations can be easily and quickly solved with the restore of missing emails (or the entire mailbox); naturally a proper backup schedule -daily, monthly and annual- must be already working flawlessly.
These first two cases are easy to identify as the lack of emails is clear and naturally leads to a timely intervention.
But there are situations where a simple backup is not enough anymore as we’ve seen in these examples.
Case 3 - Something is missing. But what?
As asked by the client, the order (or the project) has been processed. However it has been a long time from the beginning of the activity, a lot of people are involved and perhaps some of them are not even working anymore for your company. When paying, the client complains.
In order to defend your behaviour, contracts are not enough: you need to retrieve all email correspondence.
Here we face a complex scenario and we must gather all logical steps, emails and conversations and any additional agreements whose modalities or, even worse, whom they’ve been sealed with, nobody clearly remembers. Important factors as professional honesty, memory and ethical considerations on one’s own behaviour are part of the scenario, too. This situation appears more often than you might think, and backups are not the best method to deal with it.
That’s when an adequate email archiving system comes into play; the term ‘adequate’ means being compliant with the highest international standards in terms of trackability and immutability of archived emails. Some might raise a point that a backup can solve this situation, too. That’ not entirely correct: for instance, what if you scheduled a daily backup with a 15-day retention period? That means the oldest backup available is fifteen days older than the moment you realize you have a problem, which is not sufficient.
The solution to this kind of problem is archiving mailboxes on a centralized platform: all emails -intact, coherent and complete- will be available within the archive’s database for years to come.
Furthermore, the access to mailboxes and their emails can be guaranteed to users (authors) only in read mode, thus guaranteeing a priori the security of emails, which can’t be deleted as it would be with a common email client.
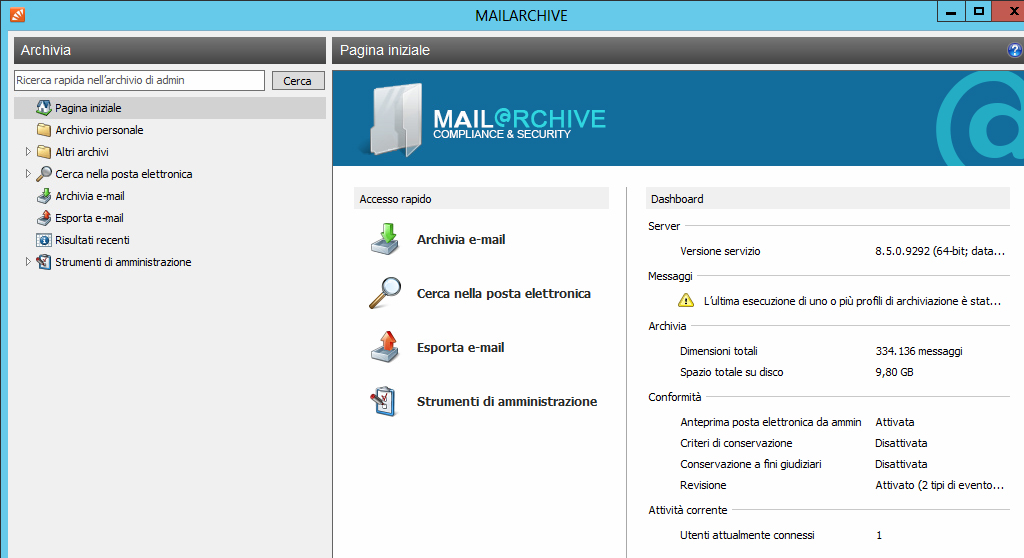
Deleting an email on the client of a specific user won’t have any effect at all on the archiving system. In a few seconds you could search among all emails sent and received to and from a certain address or containing specific keywords: if the communication actually happened, the archiving system will have recorded it, regardless to when and and who it received or sent it.
Companies which have long term agreements with clients and contracts worth tens of thousands of euros should really consider an email archiving system: it’s a well worth insurance.
With Cloud systems you can access email archiving system in a Pay-as-you-go or SaaS mode.


























