Author
The “Magic Quadrant” report for the Cloud IaaS market by Gartner is out
Gartner, the leading company in consultancy, research and analysis in the IT field, published the annual “Magic Quadrant” report for the Cloud IaaS market, which is available at this address.
Among the most interesting result we cite the first appearance of two players like Alibaba Cloud (“the vendor's potential [is] to become an alternative to the global hyperscale cloud providers in select regions over time”) and Oracle Cloud, and the disappearance of VMware vCloud Air. AWS maintains its leadership in the first quadrant, followed by Microsoft Azure: both players are the only ones to be in the “Leaders and Visionaries” quadrant, and share most of the market.
Overall, the Cloud IaaS market is described as fragmented and in a reboot phase (many providers are changing their offers and infrastructures) and, given the gap between competitors still keep on growing, some providers are specializing with specific solutions.
The Cloud market will be worth $200bln by 202
A study presented by Synergy Research Group forecasts a growth in revenues from SaaS and Cloud services with an annual average rate of 23-29% for the next five years, reaching a net value of $200 billion by 2020. This will go along with an average annual growth of 11% in the sales of infrastructures to Cloud Providers on hyperscale.
The Public Cloud sector will experience the greatest growth -29% per year- followed by Private Cloud (26%) and SaaS (23%) services. The APAC area will be the region with the biggest growth, then EMEA and North America; the most interested areas will be about databases and IaaS/PaaS services oriented to the IoT.
CommScope to purchase Cable Exchange
CommScope announces its interest in purchasing Cable Exchange, a privately held quick-turn supplier of fiber optic and copper assemblies for data, voice and video communications
Cable Exchange, headquartered in Santa Ana, Calif., manufactures a variety of fiber optic and copper cables, trunks and related products used in high-capacity data centers and other business enterprise applications.The company, founded in 1986, specializes in quick-turn delivery of its infrastructure products to customers from its two U.S. manufacturing centers located in Santa Ana, Calif. and Pineville, N.C.
As more user-driven information and commerce flows through networks, operators are quickly deploying larger and more complex data centers to support growth in traffic and transactions.
WordPress 4.8 is now available
WordPress 4.8 is now available, and this version introduces some new features: image, audio and video widgets, rich text widget for visual editing, improved link management and a new news section in the dashboard with all related WordPress events near you.
Further information are available in this post on the WordPress blog.
The update is available in the admin dashboard, we suggest to update as soon as possible but after doing a backup (just in case).
Joomla 3.7.3 is now available
Joomla has now reached version 3.7.3Joomla has now reached version 3.7.3, which is a minor release of version 3.x.
This release doesn’t introduce any new function, rather it fixes bugs and solves security issues.
In particular 2 XSS (Cross Site Scripting) and Information Disclosure vulnerabilities are fixed, which could pose a threat in terms of security.
The update is available directly within the admin dashboard.
Joomla 3.8 is expected at the end of July.
WordPress WP Statistics plugin is vulnerable to SQL Injection attacks
Suuri researchers discovered a vulnerabilitySuuri researchers discovered a vulnerability in the famous WP Statistics plugin for WordPress which permits SQL Injection attacks.
Version 12.0.9 of the plugin solves the issue, therefore we highly recommend to update the plugin as soon as possible.

According to W3Techs, WordPress is used in 28,1% of the existing Internet websites, and it accounts for 59% of those based on a CMS (Content Management System), and the adoption rate is ever increasing. These numbers alore are enough to understand the great diffusion of WordPress: its easy installation and customization make it suitable to several use cases, eCommerce shop included.
But such popularity brings a downside: it’s one of the most attractive platforms to hackers. Luckily damages of an hacking attack can be prevented and limited with techniques and best practices that we will discuss in this article.
How to protect IoT devices connected to the Internet and keep them secure
IoT is the acronym of Internet of Things, and this term defines a network where devices, sensors, objects, people and animals are equipped with a univocal ID and are capable of exchanging data through the Internet without needing a direct man-machine interaction. The idea was born from the convergence of wireless technologies and the availability of sensors and tools that are more and more small, evoluted and cheap.
This is what we wrote about IoT in our “Word of the Day” column.
On a practical side, IoT is made up by all devices connected to the Internet, and the list is very extended, as we can infer from a quick search on Shodan, the research engine for IoT devices.
A consequence of being connected to the Network is the chance of being hacked, which is not remote at all: the risk is about devices being infected and added to a botnet used for illegal stuff, like DDoS attacks, malware distribution, spam campaigns and things like these.
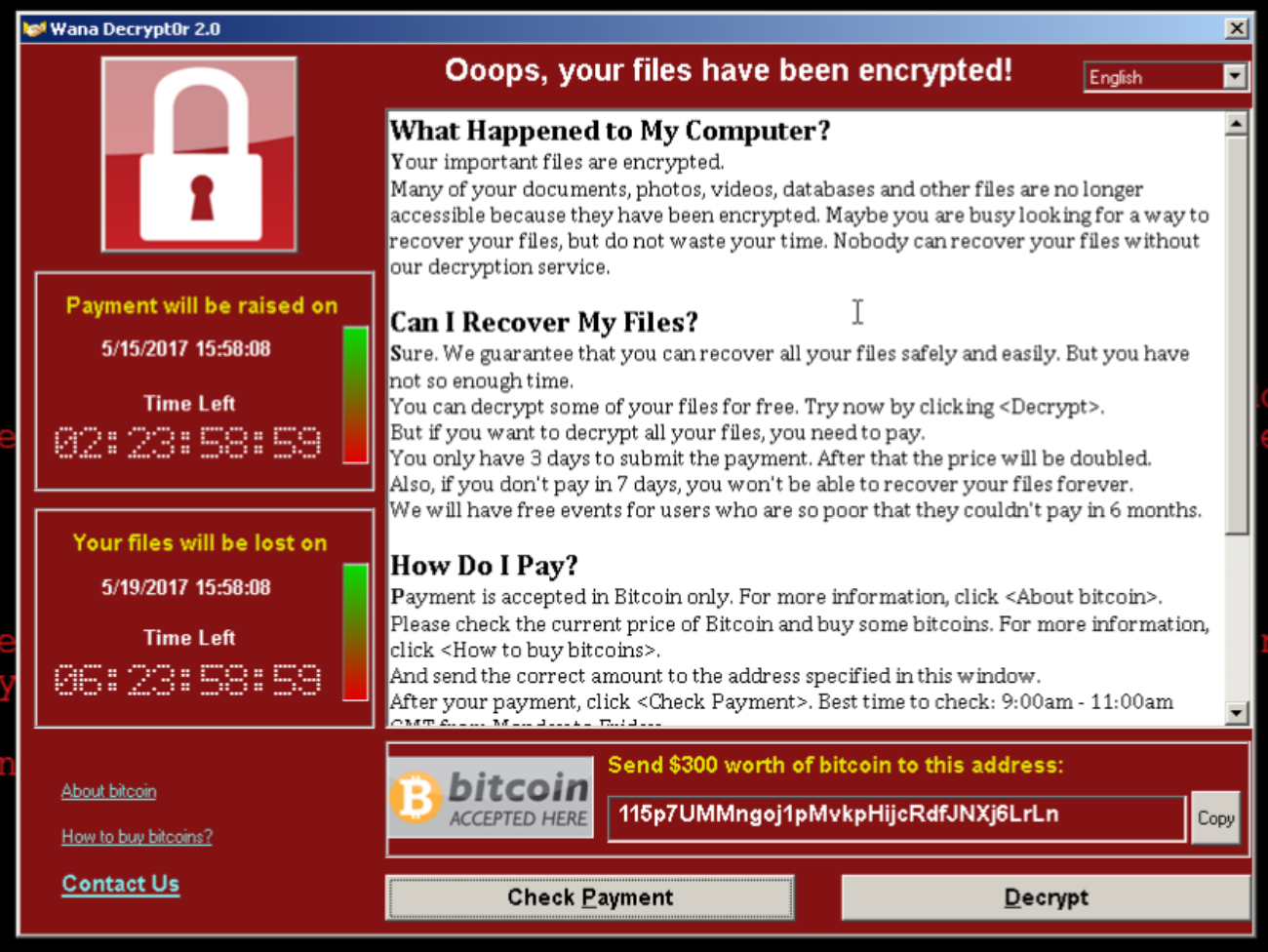
In the middle of May we witnessed an event that could have been described as a normal ransomware attack, yet it turned out to have an incredible impact: we’re talking about WannaCry.
In a few hours, this ransomware infected thousands of computers and knocked out several infrastructures before being limited. Let’s analyze what happened and why it was an attack particular in its genre and, under certain aspects, even disturbing.
Read more WannaCry: an analysis of a vicious ransomware attack
-
BYOD: your devices for your firm
The quick evolution of informatics and technologies, together with the crisis that mined financial mines, has brought to a tendency inversion: users that prefer to work with their own devices as they’re often more advanced and modern than those the companies would provide. Read More -
A switch for datacenters: Quanta LB4M
You don’t always have to invest thousands of euros to build an enterprise-level networking: here’s our test of the Quanta LB4M switch Read More -
Mobile World Congress in Barcelona
GURU advisor will be at the Mobile World Congress in Barcelona from February 22nd to 25th 2016!
MWC is one of the biggest conventions about the worldwide mobile market, we'll be present for the whole event and we'll keep you posted with news and previews from the congress.
Read More
- 1