Author
DDoS attacks and botnets
Rakos, the new botnet that attacks Linux systems
ESET researchers published an article which explain how a botnet, called Rakos, is developing by infecting Linux servers and IoT devices through SSH attacks. The Mirai botnet, as a comparison, acts via Telnet, albeit a few attacks via SSH.
The first traces of Rakos date back to August 2016 and increased in the next months: the far is that the botnet, which is not active at the moment, is in the making and will sooner or later start DDoS attacks.
ESET researchers have understood how Rakos works: first it access to a Linux server via SSH with a brute force attack and creates folder with names such as .javaxxx, .swap, or kworker and where it works from.
Read more IT Security Bulletin - January 2017An essential tool found in the toolbox of every Service Provider is remote control software, a type of software that allows to execute commands and actions on a computer situated in another place, leveraging an Internet connection. Let’s see what are the characteristics of a good remote control software, also introducing some of the available solutions.
The architecture
All remote control solutions we cover in this article are based on an architecture that calls for a host, a gateway and a client (also called guest). The host is the computer to be controlled, on which we can install an agent that sets the remote connection while being executed as service (in Windows) in order to let it run as soon as the operating system is loaded.
The client is the local computer where we can run a specific software, called viewer, which can visualize the remote screen and we use to perform operations.
If both host and client are on the same subnet, on a VPN if needed, visibility is direct and there aren’t any issue in terms of configuration and security (save for the overall network security), but if both computers are on different networks, then some problems arise as there are NAT systems to overcome and it’s mandatory to leverage at least a secure authentication and traffic encryption system for the sake of security.
In order to overcome the obstacle, a third element is introduced in the architecture: a gateway server which abstracts the connection between host and client. Such server is provided by the software produces and guarantees the proper security of connections. Solutions belonging to this review all adopt a combination of public/private key authentication and data encryption. In this way Man in the Middle (MiM) attacks are avoided and intercepted data are unusable thanks to encryption.
In the previous issues of GURU advisor we have dedicated article and in-depth analysis, like the one on the April 2016 issue, to the phenomenon of crypto-lockers. This plague isn’t showing any sign of slowing down and, if on one hand we have some good news (like the release of the code to decrypt data ciphered by TeslaCrypt), on the other hand new threats arise each week. For instance RAA, developed with JavaScripts and distributed via email as attached .doc file. Despite making it unharmful by disabling the Windows Script Host feature (and, subsequently, the execution of scripts), in practice RAA is another threats to your data. In this article we’d like to widen our knowledge by talking about specific tools to fight ransomware.
Prevention with backups, data protection, etc, still is the best tool at the disposal of users, of course.
A quick recap
There is a large number of tools we’ve already introduced you, so let’s recap them briefly.
- CryptoPrevent by FoolishIT sets Group Policy that prevent some ransomware from being installed.
- TeslaDecoder by BloodDolly decrypts files hit by TeslaCrypt (up to version 4).
- BitDefender offers a tool against Linux Encoded (a ransomware that hits Linux systems) and a vaccine for CTB-Locker, Locky and TeslaCrypt called BD Antiransomware.
- Malwaresbytes Anti-Ransomware, formerly known as CryptoMonitor, blocks CryptoWall4, CryptoLocker, Tesla, and CTB-Locker, but it’s still in beta phase.
- Third Tier Ransomware Prevention Kit contains a set of Group Policy, filters, whitelist, settings, documents and much more to prevent infections from ransomware.
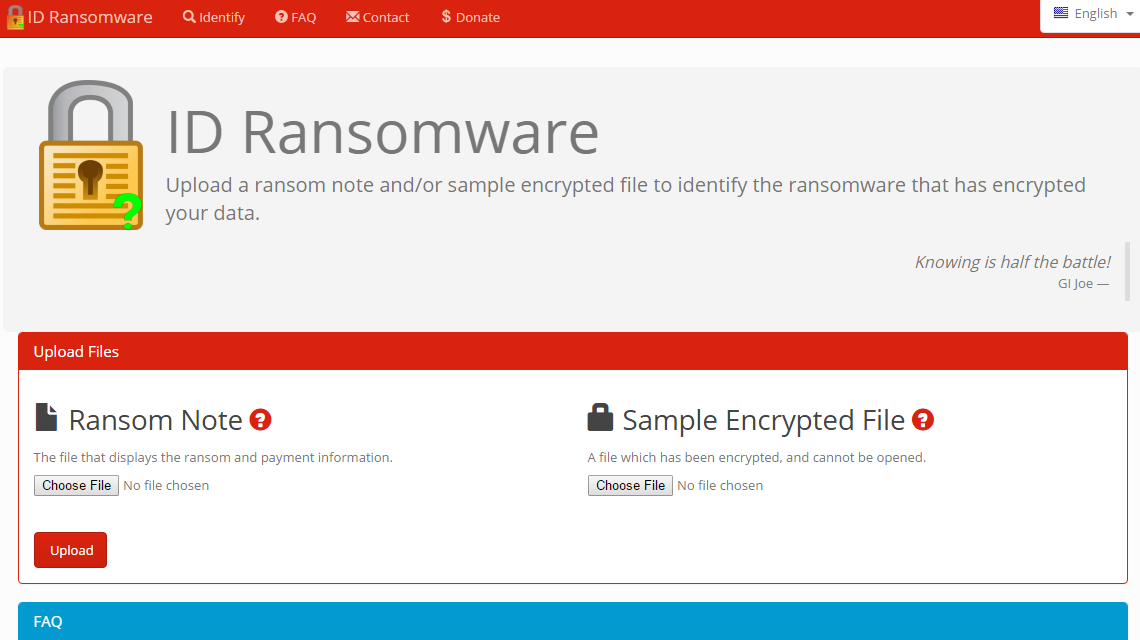
Once hit by a ransomware, the first fundamental step is to discover which crypto-ransomware is responsible for the attack. To do that, the ID Ransomware service by MalwareHunterTeam is particularly effective. By uploading an infected sample file, it identifies the type of ransomware from a pool of 103 different types available in the database. ID Ransomware doesn’t decrypt any file, it lets you know the exact nature of the ransomware attack.
Read more Anti-ransomware toolkits - How to fight Cryptolocker & CoThe quick resolution of problems is a fundamental activity for any sysadmin. Let’s discover some tricks and advices to become better and faster at diagnosing and resolving troubles of a Linux system.
In the last issues of GURU advisor we dedicated an article to those commands suitable for a basic Linux troubleshooting in a VPS context, but when top, ps and netstat are not enough, we must aim to more advanced tools. Troubleshooting is an activity that can easily transform into a waste of time and resources, proportional to the difficulties of the problems to be solved. In order to optimize the results and limit unuseful trials and tests it’s mandatory to act following well-structured procedures.
![]()
The USE method -which stands for Utilization, Saturation and Errors- was originally conceived by Brendan Gregg (who wrote an omniscient book on the topic: Systems Performance - Prentice Hall, 2013) and has its basis in a simple and efficient idea: defining a workflows that determines the level of utilization, saturation and possible errors for each available resource. In this way we can gradually reduce the number of possible causes of the misbehaviour until we can precisely identify the cause of the loss of performance.
Defining resources is quite easy: they are the physical components of a machine (we can apply the method to software components, but it would get very complicated and detailed -- perhaps a bit too overkill given the scenario), a server in our case -and the equivalent virtual version. Processor, memory, disk, controllers, network interfaces, buses, etc..
Naturally the better the knowledge of the architecture, and the faster and more precise the results will be, albeit implying a certain complexity and a steep learning curve.

Cloud's future is hybrid, according to HPE
Jorge Colotto, VP Communications Service Providers, talks about HPE and the choice of adopting OpenNFV solutions and open technology standards.
During our visit at the Mobile World Congress in Barcelona, we also stopped at the Hewlett Packard Enterprise stand, the new company born from the recent split of HP in two parts. Regardless HPE being a smaller company than HP, its presence at MWC is massive, a whole lotta 3 stands, of which one is dedicated to NFV (Network Function Virtualization) partners.
We have interviewed Jorge L. Colotto, VP Communications Service Providers Industry, and talked about some of the news of this MWC and its point of view regarding the IT world.
Jorge, what are the points of reference for the new HPE in this world that is ever shifting towards the mobile sphere? In a world that is more and more addressing towards IT, like Telco’s, do you believe that security is sufficiently taken into account?
Read more Cloud's future is hybrid, according to HPE - Interview with Jorge Colotto of HPE-
BYOD: your devices for your firm
The quick evolution of informatics and technologies, together with the crisis that mined financial mines, has brought to a tendency inversion: users that prefer to work with their own devices as they’re often more advanced and modern than those the companies would provide. Read More -
A switch for datacenters: Quanta LB4M
You don’t always have to invest thousands of euros to build an enterprise-level networking: here’s our test of the Quanta LB4M switch Read More -
Mobile World Congress in Barcelona
GURU advisor will be at the Mobile World Congress in Barcelona from February 22nd to 25th 2016!
MWC is one of the biggest conventions about the worldwide mobile market, we'll be present for the whole event and we'll keep you posted with news and previews from the congress.
Read More
- 1
























