- Details
-
Category: VMworld
-
Published: Monday, 26 October 2015 09:11
-
Written by Filippo Moriggia

Among the people we have met for you at VMworld 2015, there’s Itai Greenberg, Head of Datacenter Security Business for Check Point.
Good day Itai, let’s start with a brief introduction of the company, for those who don’t know Checkpoint yet and its role in the world of security.
Check Point is an Israeli company, the absolute leader in its sector, it protects more than 100.000 companies and covers all the levels of security, from Mobile to Cloud, through Datacenter. As we are at VMworld, I’d like to highlight that our coverage for hypervisors and our Software-Defined protection are total: we support NSX as well, the protection on a hypervisor level and we can promptly intervene on VM by locking the connections to a network if a malicious infection is revealed.
How do you manage the protection of mobile devices? By means of a traditional anti-virus program?
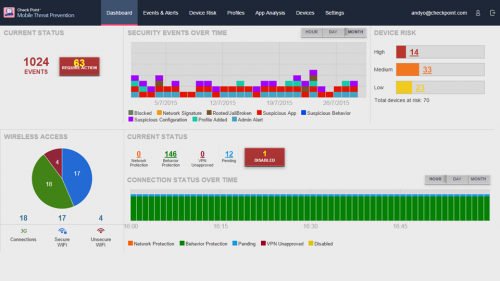 The Dashboard of Check Point's Mobile Threat Prevention No, the protection of mobile devices is fundamental for us, so we use an extremely sophisticated solution called Check Point Capsule: it’s a separated environment dedicated to the business applications that runs inside smartphones and tablets (Android and iDevices) and can handle emails, contacts, agenda, notes, shared files and Remote Desktop connections with no level of interaction with the main applications installed on devices. Aiming for a BYOD (Bring Your Own Device) finally secure and protected. A management connection for controlling terminals in a centralized way is naturally present.
The Dashboard of Check Point's Mobile Threat Prevention No, the protection of mobile devices is fundamental for us, so we use an extremely sophisticated solution called Check Point Capsule: it’s a separated environment dedicated to the business applications that runs inside smartphones and tablets (Android and iDevices) and can handle emails, contacts, agenda, notes, shared files and Remote Desktop connections with no level of interaction with the main applications installed on devices. Aiming for a BYOD (Bring Your Own Device) finally secure and protected. A management connection for controlling terminals in a centralized way is naturally present.
Do you have a managed solution of your product for desktop and servers? Do you allow Managed Service Providers and resellers to manage the situation of their own clients without having to access to a multitude of console, one after another?
Surely, our product can be managed by resellers -and their clients- when we are in an environment where an internal IT is present, and by Check Point itself for Cloud based solutions.
Do you have any technology that goes beyond the traditional antivirus protection? To overcome the concept of identification with signatures and obtaining a more prompt time of intervention? For instance, in the case of Ramsonwares like Cryptolocker?
Check Point Sandblast, included in our Next Generation Prevention line, is a proprietary technology that aims to that goal. The recent attacks often use well-known vulnerabilities and modified signature to avoid to be identified.
The variations that are created allow to not be identified by traditional antiviruses. Sandblast offers a protection to 0-day attacks by identifying exploits on a CPU level and a prompt protection against malware not already revealed.