With a coup de théâtre like in a spy movie, the developers behind the feared TeslaCrypt ransomware finally decided to end its development and diffusion project and openly published an universal key to decrypt files.
In an article on last month’s issue we dealt with the ransomware phenomenon: TeslaCrypt is for sure one of the most feared and widespread virus of this kind. Luckily, we have a good news: an universal decryption key is available and ready to be used by those who have been infected by this virus.
A researcher of Eset -the renown software house that develops the Eset antivirus- contacted the developers of TeslaCrypt with the support chat of the ransom payment portal and, pretending to be an user hit by the ransomware, asked for a decryption key. With his uttermost surprise, he was delivered with the universal alphanumeric decryption key. Naturally a proper tool is needed in order to use such key, and this problem has been solved too: the developer BloodDolly, who released months ago his TeslaDecoder tool to decrypt files hit by the first versions of TeslaCrypt (1.0 and 2.0), updated his tool so it can now decrypt files created by versions 3.0 and 4.0 of the dangerous ransomware (the ones with extensions .xxx, .ttt, .micro, .mp3 or even without any extension at all).
Finally a good news for those who kept a copy of the encrypted files, as we always advise to do.
Let’s see how to download and use the decryption tool.
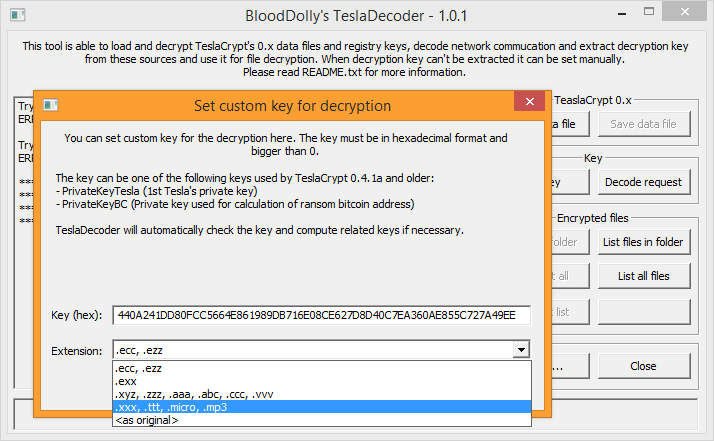
You can obtain the program at this link: it’s a .zip archive with an HTML instruction page, a folder with the screenshots of the steps to follow and 3 executable files. The first one is TeslaCrypt: this component analyzes the encrypted files provided as an example and extracts the keys SharedSecret1*PrivateKeyBC and PublicKeyBC, which are needed for the next steps. TeslaRefactor creates a private decryption key from the two previously extracted and factorized keys. Lastly TeslaDecoder, by leveraging the whole key, decrypts each compromised available file.
This procedure holds for versions 1.0 and 2.0 of the ransomware, while the release of the universal key makes unnecessary the use of the first two tools for those files hit by the last two releases, as all you need to do is to execute TeslaDecoder and use the key provided by the developers (440A241DD80FCC5664E861989DB716E08CE627D8D40C7EA360AE855C727A49EE).
This great news is a perfect companion with the release, a few weeks ago, of a tool by Kaspersky to decrypt files hit by CrypXXX. Naturally the news about these two programs is the only good aspect in a situation that is negative as a whole, as the phenomenon keeps on growing. At the moment, according to experts, the most dangerous ransomware is Locky, discovered at the beginning of the year.
