- Details
-
Published: Thursday, 08 June 2017 15:11
-
Written by Riccardo Gallazzi
DDoS attacks and botnets
Rakos botnet grows but remains dormant
The Rakos botnet grows but remains inactive, Morphus Labs’ Renato Marinho says.
Rakos adds 8.000 new zombie IoT each day, and continues to evolve: it now has a P2P structure. Some bots act as a (Command & Control) called Skaros, while other act as “slaves” -Checker- and launch SSH attacks to targets to add them to the botnet.
Today Rakos is composed by IoT devices as Raspberry PI (45%), OpenELEC on Raspberry PI (22%), Ubiquiti wireless access points (16%) and other.
As of now, the only remedy to the malware is to reboot the IoT device and use strong SSH credentials.
Marinho defines the botnet as “transient”: bots don’t remain as such indefinitely but only until a reboot. The force of the botnet lies in the number of bots available each day -almost 8.000- which is enough to launch an impactful DDoS attack.
Shodan launches new tool to find C&C servers
Shodan launches Malware Hunter, a tool specifically conceived to find Command and Control (C&C, sometimes C2) servers, ie servers belonging to a botnet that send commands to zombie members of the net and act as malware download center.
Malware Hunter works thanks to bots that scan the Network looking for computer configured to act as a C2 server; bots then use a predefined mode pretending to be an infected computer and communicate with the suspected C&C server: if it replies, Malware Hunter records data and makes it available with its powerful graphical tool.
Read more ...
- Details
-
Published: Monday, 10 April 2017 12:21
-
Written by Riccardo Gallazzi
DDoS attacks and botnets
Mirai botnet launches DDoS attack toward US college
At the end of March Incapsula researchers discovered a DDoS attack aimed to an UN college.
The attack lasted 54 hours and generated an average of 30.000 requests per second with a peak of 37.000 and a total of 2.8bln requests; such number can KO most devices on the network.
Less than a day after the first attack, a second one happened, but this time with a lower impact: it lasted a little bit more than an hour and a half and RPS were 15.000, on average.
The attack shows a probable new version of the Mirai botnet, as the dimensions of the attack itself and used agent users show; it had an impact on the application level rather than on the network layer.
9.793 different IP addresses (from the US, Israel, Taiwan, India, Turkey, Russia and Italy) belong to Internet of Things devices like CCTV cameras, router and DVRs; in particular, 56% of the devices belongs to a DVR model of a single manufacturer.
Read more ...
- Details
-
Published: Monday, 10 April 2017 12:21
-
Written by Riccardo Gallazzi
DDoS attacks and botnets
Linux.MulDrop14 targets Raspberry-PI devices for cryptocurrencies mining
Dr.Web researchers discovered a malware, called Linux.MulDrop14, which targets Raspberry PI devices, the popular single board computer, adding them to a botnet that mines for cryptocurrencies.
In this case devices which still have default credentials and are reachable via SSH from the outside are vulnerable: the malware installs on the device, changes the access password and adds some packages, including libraries to start mining, ZMap to scan networks for vulnerable devices and sshpass to login on any found device.
Once infected, the only way to delete the malware is reinstalling the whole operating system. Naturally default passwords must be changed.
Read more ...
- Details
-
Published: Friday, 03 February 2017 14:26
-
Written by Lorenzo Bedin
The second edition of the Security Barcamp organized by Trend Micro proves to be a very interesting meeting about IT related topics, both on a worldwide and on a more Italian-focused scale.

Rik Ferguson, Trend Micro Vice-President, was the special guest of the event and, in an extended speech, he spoke about the three main threats in the IT field of the moment and which will be in the future.
The most important threat is ransomware for sure. The phenomenon boomed in 2015 and experienced a 400% growth in terms of attack typologies and available families during the following year. The new trend is to refine and improve the attacking techniques with a particular focus on selected business targets (whose data have an important value and can justify the payment of the ransom) and social engineering, which is at the basis of these attacks.
Read more ...
- Details
-
Published: Monday, 16 January 2017 12:21
-
Written by Riccardo Gallazzi
DDoS attacks and botnets
Rakos, the new botnet that attacks Linux systems
ESET researchers published an article which explain how a botnet, called Rakos, is developing by infecting Linux servers and IoT devices through SSH attacks. The Mirai botnet, as a comparison, acts via Telnet, albeit a few attacks via SSH.
The first traces of Rakos date back to August 2016 and increased in the next months: the far is that the botnet, which is not active at the moment, is in the making and will sooner or later start DDoS attacks.
ESET researchers have understood how Rakos works: first it access to a Linux server via SSH with a brute force attack and creates folder with names such as .javaxxx, .swap, or kworker and where it works from.
Read more ...
- Details
-
Published: Wednesday, 29 June 2016 18:03
-
Written by Filippo Moriggia
Here’s how to use SSL/TLS, S/Mime, certificates and public key cryptography in order to make Web services and email communications safer
Despite several technologies related to SSL/TLS protocols being attacked in the last 3 years, a good sysadmin or IT manager in 2016 can’t tolerate its organization still uses systems that transmit information in clear.
The use of Transport Layer Security (and its predecessor SSL) -it should be clear- it not enough to guarantee confidentiality of transmitted data on the Internet, and a quick bibliographic research shows the vast method of attacks to such protocols (like in this case and this other). TLS represents a first, fundamental security level for transmitted data, both for the access of a Web service of your company and the access to email via Webmail or IMAP/POP3/Exchange.
TLS acts as a tunnel and doesn’t modify the ongoing communication between client and server: it only adds a layer, indeed, that ciphers data between the source and the destination by using some key concepts at the basis of public key cryptography. Who has a server role needs a certificate, released by a certification authority or, in the worst case, self-signed: only who has purchased the certificate owns the private key that allows to encrypt the communication.
Read more ...
- Details
-
Published: Wednesday, 29 June 2016 17:58
-
Written by Riccardo Gallazzi
In the previous issues of GURU advisor we have dedicated article and in-depth analysis, like the one on the April 2016 issue, to the phenomenon of crypto-lockers. This plague isn’t showing any sign of slowing down and, if on one hand we have some good news (like the release of the code to decrypt data ciphered by TeslaCrypt), on the other hand new threats arise each week. For instance RAA, developed with JavaScripts and distributed via email as attached .doc file. Despite making it unharmful by disabling the Windows Script Host feature (and, subsequently, the execution of scripts), in practice RAA is another threats to your data. In this article we’d like to widen our knowledge by talking about specific tools to fight ransomware.
Prevention with backups, data protection, etc, still is the best tool at the disposal of users, of course.
A quick recap
There is a large number of tools we’ve already introduced you, so let’s recap them briefly.
- CryptoPrevent by FoolishIT sets Group Policy that prevent some ransomware from being installed.
- TeslaDecoder by BloodDolly decrypts files hit by TeslaCrypt (up to version 4).
- BitDefender offers a tool against Linux Encoded (a ransomware that hits Linux systems) and a vaccine for CTB-Locker, Locky and TeslaCrypt called BD Antiransomware.
- Malwaresbytes Anti-Ransomware, formerly known as CryptoMonitor, blocks CryptoWall4, CryptoLocker, Tesla, and CTB-Locker, but it’s still in beta phase.
- Third Tier Ransomware Prevention Kit contains a set of Group Policy, filters, whitelist, settings, documents and much more to prevent infections from ransomware.
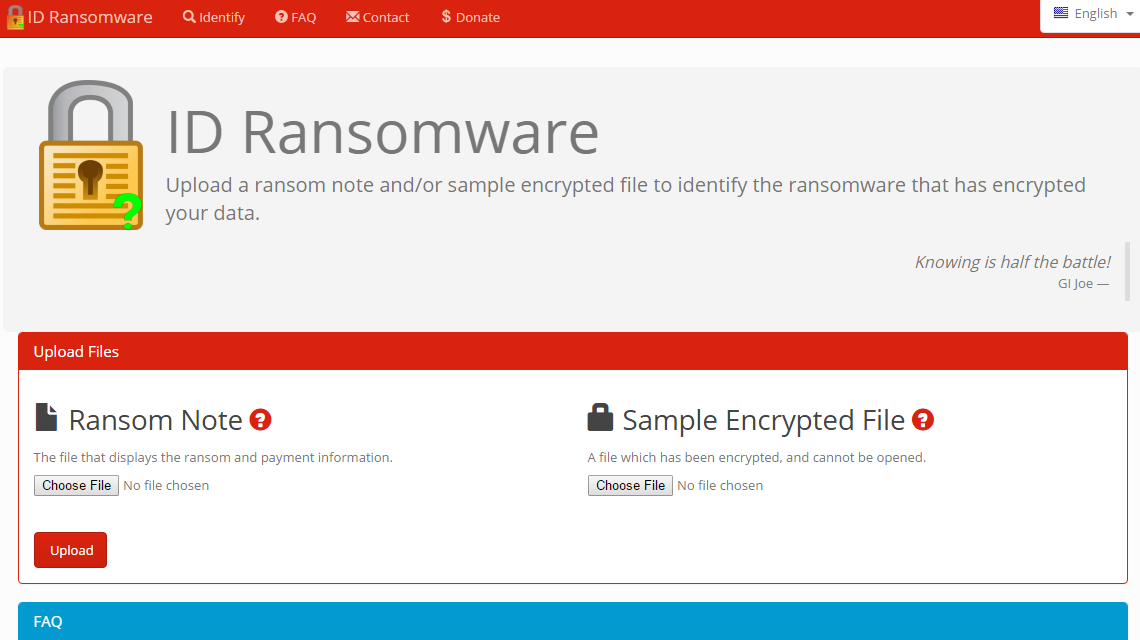
Once hit by a ransomware, the first fundamental step is to discover which crypto-ransomware is responsible for the attack. To do that, the ID Ransomware service by MalwareHunterTeam is particularly effective. By uploading an infected sample file, it identifies the type of ransomware from a pool of 103 different types available in the database. ID Ransomware doesn’t decrypt any file, it lets you know the exact nature of the ransomware attack.
Read more ...
- Details
-
Published: Wednesday, 29 June 2016 17:46
-
Written by Veronica Morlacchi
Perhaps you did underestimate them, but all virus, and in particular, the more recent Ranswomare that steal your data and ask for a ransom, are against the law. Let’s see how to behave, and let’s understand when and if filing a complaint.
As a technician, expert, IT manager or consultant you’ve maybe given advice to your colleagues, friends and clients by facing legal questions related to the IT world with a practical approach, using some common sense. Unfortunately that could not be the best way to follow, at least if you want to avoid risks, damages or consequences on your activity.
Warning: while the reflections contained in this article apply to Italian law, they may or may not apply to other laws. Each specific italian term is specified in parenthesis for a better understanding.
All malware -that is, harmful software that snake into computers and IT systems to steal information, open ports for remote control and other perils, or encrypt data with an extortion aim- clearly violate the italian juridical system and who spreads them commits a crime which is subject to sanctions according to our penal code (codice penale, c.p.). In particular, there is not only an abusive access to an IT or telematic system (ex art.615 ter c.p.), but also the diffusion of devices or programs with the specific fraud (that is, consciously) of damaging, interrupting or altering any IT or telematic system, and we can also face the criminal hypothesis of art.615 quinquies c.p.; if a “damagement of information, data and programs” is present, the crime is condemned by art.635 bis c.p. with a basic punishment of detention for 6 months to 3 years, complaint presented, with respect to art.124 c.p., within 3 months to the news of the crime (otherwise, prosecution cannot be advanced).
But things worsen if we deal with the recent threats brought by ransomware, virus that encrypt files and ask for a ransom in order to have decryption keys. In this case it’s a crime, still not specified in the IT world, of extortion, which is regulated by art.629 c.p., in accordance with the indications given by the Ministry of Justice (Ministero della Giustizia). The crime of extortion if committed by “whoever, by means of violence or threat, obliging someone to do or omit something, gains himself or others an unfair profit with damage to a third party.” From that it would derive stricter penalties to the responsibles (basic penalty is detention from 5 to 10 years and a fine from 1.000 to 4.000€), in addition the crime to being prosecutable ex officio. Moreover, it would also derive, from the transfer of money of the ransom payment, the crime of laundering (riciclaggio) ex art.648 bis c.p. in charge to who has received and “used” money.
How to behave if hit by malware or ransomware?
Read more ...
- Details
-
Published: Friday, 20 May 2016 18:32
-
Written by Lorenzo Bedin
With a coup de théâtre like in a spy movie, the developers behind the feared TeslaCrypt ransomware finally decided to end its development and diffusion project and openly published an universal key to decrypt files.
In an article on last month’s issue we dealt with the ransomware phenomenon: TeslaCrypt is for sure one of the most feared and widespread virus of this kind. Luckily, we have a good news: an universal decryption key is available and ready to be used by those who have been infected by this virus.
A researcher of Eset -the renown software house that develops the Eset antivirus- contacted the developers of TeslaCrypt with the support chat of the ransom payment portal and, pretending to be an user hit by the ransomware, asked for a decryption key. With his uttermost surprise, he was delivered with the universal alphanumeric decryption key. Naturally a proper tool is needed in order to use such key, and this problem has been solved too: the developer BloodDolly, who released months ago his TeslaDecoder tool to decrypt files hit by the first versions of TeslaCrypt (1.0 and 2.0), updated his tool so it can now decrypt files created by versions 3.0 and 4.0 of the dangerous ransomware (the ones with extensions .xxx, .ttt, .micro, .mp3 or even without any extension at all).
Read more ...
- Details
-
Published: Monday, 18 April 2016 19:44
-
Written by Filippo Moriggia
When preparing this article we’ve asked to all the main security firms to explain which technologies or tools they offer for ransomware protection. Common signature-based antiviruses are not enough to be protected as these malware are custom-tailored for every attack and the executable is masked and modified in different ways, so that it always appears as a different version.
You already know the most obvious advice: keep Windows, antivirus and all the main software (including tools like Flash, Java and Adobe Reader which are often an attack medium) up to date.
Let’s see what information we have collected from the security firms that have replied us.
Avast, mostly known for its antivirus, talked with us about DeepScreen: this technology, part of all desktop products since the 2014 version, is based on the sandbox principle. Potential malware is first executed in a sandbox to evaluate its behaviour. According to Avast, malware uses new technologies to escape from this kind of protection, but its engine is continuously updated together with definitions, so it always includes the latest control features to avoid being deceived with a clever trick.
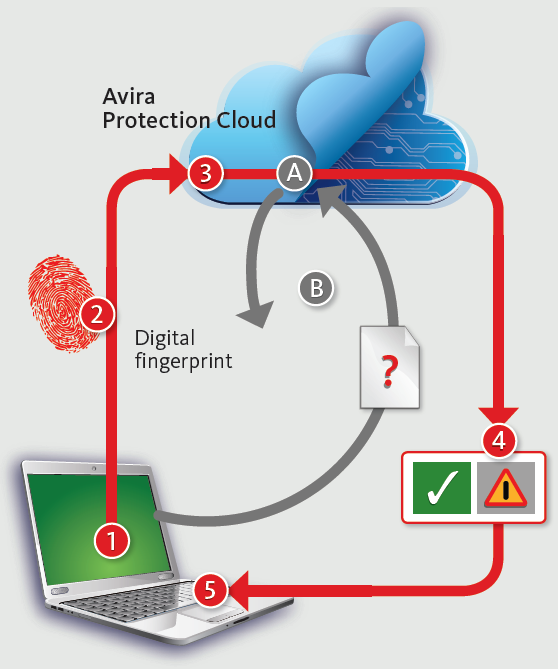
Avira recommends to activate the Cloud-based protection (Avira Protection Cloud -- see the image on the side). This technology sends a fingerprint of suspicious files to the laboratories of this famous security firms to check if it’s an already analyzed executable. If the file is not recognized it’s immediately uploaded online and analyzed. Avira leverages several techniques to overcome the anti-debugging and anti-sandboxing technologies implemented by malware.
Read more ...