When preparing this article we’ve asked to all the main security firms to explain which technologies or tools they offer for ransomware protection. Common signature-based antiviruses are not enough to be protected as these malware are custom-tailored for every attack and the executable is masked and modified in different ways, so that it always appears as a different version.
You already know the most obvious advice: keep Windows, antivirus and all the main software (including tools like Flash, Java and Adobe Reader which are often an attack medium) up to date.
Let’s see what information we have collected from the security firms that have replied us.
Avast, mostly known for its antivirus, talked with us about DeepScreen: this technology, part of all desktop products since the 2014 version, is based on the sandbox principle. Potential malware is first executed in a sandbox to evaluate its behaviour. According to Avast, malware uses new technologies to escape from this kind of protection, but its engine is continuously updated together with definitions, so it always includes the latest control features to avoid being deceived with a clever trick.
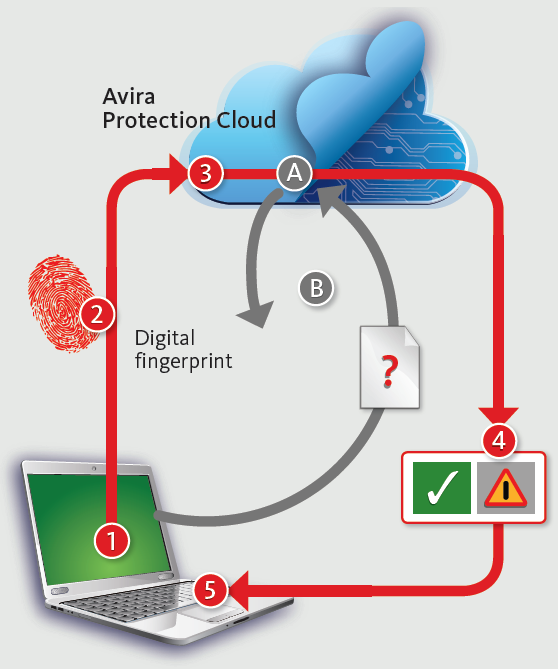
Avira recommends to activate the Cloud-based protection (Avira Protection Cloud -- see the image on the side). This technology sends a fingerprint of suspicious files to the laboratories of this famous security firms to check if it’s an already analyzed executable. If the file is not recognized it’s immediately uploaded online and analyzed. Avira leverages several techniques to overcome the anti-debugging and anti-sandboxing technologies implemented by malware.
Bitdefender includes in its desktop product line some anti-malware specific technologies: its engine (also with the Antivirus Plus release) can identify when a software quickly (and suspiciously) accesses several files of a computer and blocks it asking the user what to do. This protection can be extended to external disks but not to network shares. A second free and compatible with any antivirus tool is simply called Bitdefender Anti-Ransomware. This tools exclusively protects against Cryptowall, CTB-Locker, Locky and TeslaCrypt but it’s completely free and its installation takes only a few seconds. It’s like a vaccine: it tricks these virus making them believe they're running on an already attacked system. We also suggest the useful Decryption Tool for the Linux Encoder virus (which plagues Linux machines) released by Bitdefender itself.
ESET, the Slovak software house that develops the infamous NOD32 antivirus, told us the protection happens with signatures and with its file reputation system called Live Grid. This component works together with two other tools: Advanced Memory Scanner and Exploit Blocker. The latter checks all the processes looking for behaviours typical of exploits, while the former looks for suspicious behaviours when malware is executing. ESET also suggests to disable the RDP access where it’s not needed and to set email servers to block executable files and to disable the execution of files within the AppData and LocalAppData folders.
Fortinet, the company famous for its Fortigate line, gateways based on physical or virtual appliances to protect networks, suggests to activate the Antivirus/Antimalware and Application Control modules: the arrival of suspicious files or non-authorized applications can be blocked directly on a network level. By activating the Advanced Threat Prevention (ATP), FortiSandbox can analyze the behavior of potentially suspicious files in a controlled area (a sandbox, indeed) and block them in case an an anomalous behaviour.
Kaspersky Labs suggests to activate the Application Control feature of Kaspersky Internet Security to protect from malware that are not filtered with signatures. After an infection, if no updated backup is available, some tools are available at https://noransom.kaspersky.com. Unfortunately there are a few keys and supported cryptoviruses available on this portal, born as a collaboration with the Netherlands' police, still it’s worth a visit.
McAfee -now an Intel property- sent us a detailed report about technologies implemented in their products and that are effective against ransomware. GTI (Global Threat Intelligence) is the technology at the basis of continuous updates related to file reputation. The email gateway by McAfee filters suspicious messages and blocks dangerous links thanks to ClickProtect. VirusScan’s Enterprise line products can not just identify ransomware, but also remove the main ones.
Sophos, an important software house that develops some of the most known and used antiviruses and UTMs, sent us an extremely detailed documentation of the ways of diffusion of ransomware. The conclusions drawn by Sophos are very savvy: a complete protection can arise only from a combination of technologies that fight the different spreading types of these software. The family of technologies that is dedicated to the protection of users from such malware is Sophos HIPS (Host Intrusion Prevention System). This proactive technology controls the behaviour and constantly monitors the system by checking the access to files, renaming operations and accesses to the Windows register. According to each analyzed threat (the document we received deals with Cryptowall, TorrentLocker, TeslaCrypt and CTB-Locker), the Sophos HIPS technology uses specific signatures that analyze the typical behaviours of each ransomware. These signatures don’t require frequent updates because they are generic and not related to the hash of a file, as in the case of traditional antiviruses. Sophos also suggests to block at the gateway level the access to Tor, I2P and other networks that are exploited by this kind of malware.
Symantec, the company behind the infamous Norton Antivirus, explained us that STAR (Security Technology And Response) is at the basis of the protection against ransomware of the Norton product line. This technology includes protection techniques related not just to traditional signatures but also to network traffic analysis, application behaviours and to a reputation system that evaluates the danger risks of a file based on its age, origin and spread. A quick response is fundamental with this kind of technologies, therefore Symantec has a worldwide network of technicians with a coverage of 130 million systems and 240.000 network sensors in more than 200 countries.
Trend Micro is one of the most active security firms in the business world and has released a plenty of documentation regarding ransomware on its blog (http://blog.trendmicro.com). Its Browser Exploit Prevention blocks all the attacks at the browser layer on all endpoints, in particular on the Trend Micro Security, Smart Protection Suite and Worry-Free Business Security product lines. Moreover, its products include a sandbox with an script analysis system that is part of the Deep Discovery technology of Trend Micro itself. This technology directly analyzes the behaviour of applications and takes advantage of an update system that differs from the one of traditional antiviruses which is based on patterns.
Vir.it explained us that the euristic-behavioural technologies included in their antivirus can block a virus when it starts to encrypt files. At the same time the Backup-on-the-fly tools included in the suite protect all the files modified within the last 48 hours with an automated backup system that guarantees that no file can get lost.
Webroot is an antivirus that natively works without any traditional signature by leveraging the Cloud. All the applications are uploaded online and their validity is verified, thus offering a native protection against the threats of ransomware. In addition to that, Webroot leverages a database of information on suspicious IP addresses and harmful URLs and blocks every connection attempt to dangerous sites. The integrated journaling and roll-back features allow to go back in time should some non identified application intervene on the system. If a not identified application is marked as dangerous, Webroot can bring the system to the state previous to its execution.
Continues from: ransomware, secure backups and specific tools
Related: the latest news and how to behave if infected