Author
Lorenzo Bedin
Lorenzo graduated in Telecommunication Engineering and works as freelance IT consultant, after a period of training as systems analyst. Currently he provides hardware solutions, virtualized infrastructures and websites.
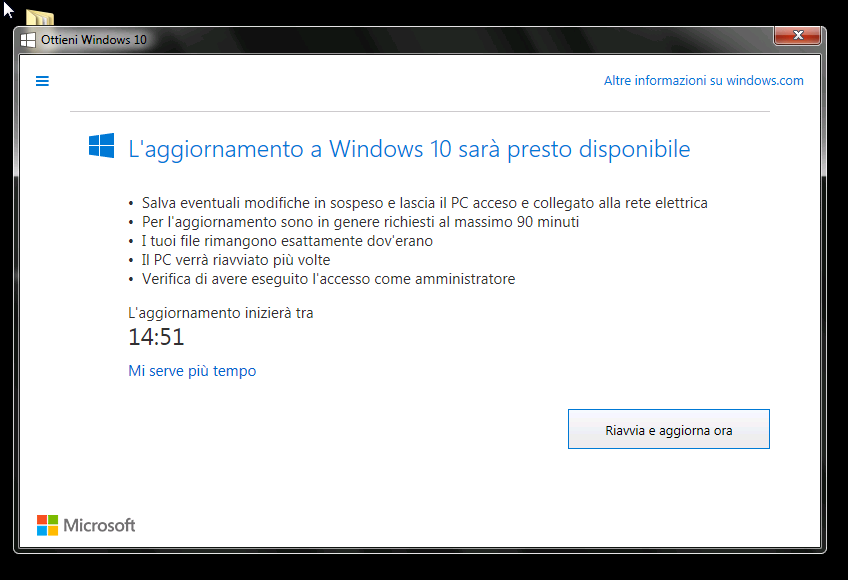
The release of a new operating system is an usual scenario for IT pros. The release of Windows 10 is no exception to that, but the way of distribution experimented by Microsoft has certainly changed.
For the first time in the history of the OS from Redmond, users of the previous of Windows (7, 8 and 8.1) can download and install for free the upgrade to Windows 10, naturally maintaining an equivalent version to the one previously installed (ie. 7 Professional becomes 10 Pro) and related license. However the insistent distribution method has beared a certain dissatisfaction amongst users and professionals. This feeling is also emphasized by the integration of the Windows 10 update straight into Windows Update (which results in an automated installation in most cases) and by the pounding notification campaigns for non-updated computers.
The term MSP is the acronym for Managed Service Provider and identifies a working method nowadays used by many companies in the IT world. In general, the idea of Managed Service implies an outsourcing approach of management and maintenance activities with the ultimate goal of optimizing the use of resources and lowering costs of the client. In this scenario, the Provider is the company or society that provides the service.
MSP key points
We can define three main points that characterize a Managed Service Provider (MSP onwards):
- unlimited phone/remote help desk;
- proactive management of the infrastructure: backup, security, updates, etc..;
- being a competent intermediary with additional providers and third parties.

Advantages and rates
Essentially a MSP contract is an “all-inclusive” contract with reciprocal advantages for both the provider and the client. In this way the client can have a fixed price for IT management, without worrying about any technical aspect or surprise about costs. Moreover, the client is aware the goal of the provide is the same of his own, ie to reduce down times and increase the overall productivity of the company.
Read more Managed Service Provider: what it means, why becoming a MSPThe intent of VMware, in the long run, to definitely ditch the C# based Windows client in favour of a Web client has been clear for a long time: and a few days ago the announce appeared on the official blog, with all the reasons about this choice and the news of the new product. (download it here).
The first statement regards the availability of the old Windows client that, starting with the next release of the popular hypervisor, won’t be supported anymore (but it will continue to work as expected with the previous versions up to 5.5 and 6.0), and the other is about the complete migration from Flash to HTML5, concerning the language the interface is developed with.
With a coup de théâtre like in a spy movie, the developers behind the feared TeslaCrypt ransomware finally decided to end its development and diffusion project and openly published an universal key to decrypt files.
In an article on last month’s issue we dealt with the ransomware phenomenon: TeslaCrypt is for sure one of the most feared and widespread virus of this kind. Luckily, we have a good news: an universal decryption key is available and ready to be used by those who have been infected by this virus.
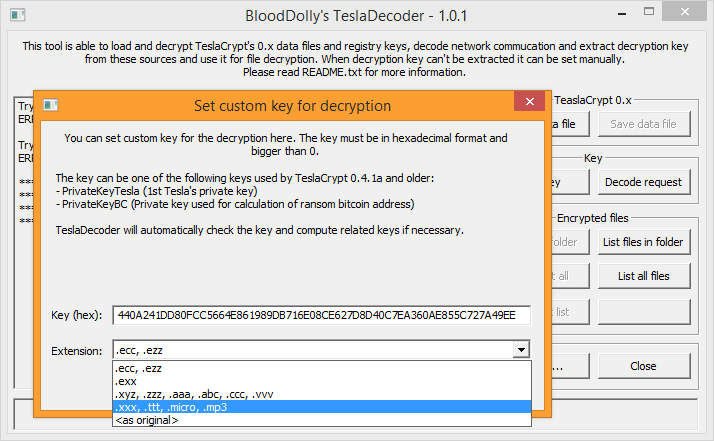
A researcher of Eset -the renown software house that develops the Eset antivirus- contacted the developers of TeslaCrypt with the support chat of the ransom payment portal and, pretending to be an user hit by the ransomware, asked for a decryption key. With his uttermost surprise, he was delivered with the universal alphanumeric decryption key. Naturally a proper tool is needed in order to use such key, and this problem has been solved too: the developer BloodDolly, who released months ago his TeslaDecoder tool to decrypt files hit by the first versions of TeslaCrypt (1.0 and 2.0), updated his tool so it can now decrypt files created by versions 3.0 and 4.0 of the dangerous ransomware (the ones with extensions .xxx, .ttt, .micro, .mp3 or even without any extension at all).
Pritunl is an open source platform capable of realizing distributed VPN networks. By leveraging the OpenVPN protocol it allows -according to the chosen licensing model- to setup virtual network architectures. In practice, it allows to easily connect devices inside or outside the walls, also in companies with two or more branches, creating a VPN managed with advanced rules and a centralized authentication system.Pritunl integrates several services of third parties like Amazon AWS VPC (Virtual Private Cloud, it’s a virtual network space in the Cloud available to users within the AWS suite) with automated failover and Single Sign On (SSO) authentication. Integration for the use of SSO include services like Google Apps, Slack, OneLogin Okta, DUO and Radius: each one of these service can be used to guarantee users the access to the Pritunl infrastructure with their own accounts and without having to use dedicated credentials. In case the Enterprise license is chosen, which allows the installation on an unlimited number of Pritunl server, the high availability with automated failover feature can be leveraged, also given the fact that there are no master nodes, instead each node acts as the same functional level of the others. Pritunl also integrates a server replication feature, thus offering an high level of scalability for clusters. With the aim of geographically distributed installations, the platform is based on the renowned MongoDB which offers an high level of reliability (in particular as the number of nodes and users grows) associated with the chance of replication.
Read more Pritunl: an enterprise and on-premises SDN based on OpenVPN-
BYOD: your devices for your firm
The quick evolution of informatics and technologies, together with the crisis that mined financial mines, has brought to a tendency inversion: users that prefer to work with their own devices as they’re often more advanced and modern than those the companies would provide. Read More -
A switch for datacenters: Quanta LB4M
You don’t always have to invest thousands of euros to build an enterprise-level networking: here’s our test of the Quanta LB4M switch Read More -
Mobile World Congress in Barcelona
GURU advisor will be at the Mobile World Congress in Barcelona from February 22nd to 25th 2016!
MWC is one of the biggest conventions about the worldwide mobile market, we'll be present for the whole event and we'll keep you posted with news and previews from the congress.
Read More
- 1
























