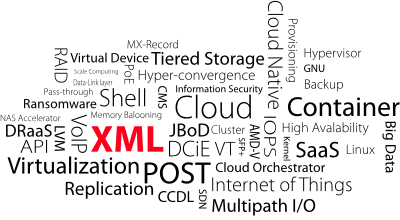- Details
-
Category: Word of the Day
-
Published: Wednesday, 19 April 2017 17:34
-
Written by Guru Advisor
The acronym UAT stands for User Acceptance Testing and decribes the final part of software development. In this phase the product is given to users of a sample with the aim of simulating a real usage and determining a behaviour in a realistic scenario.
- Details
-
Category: Word of the Day
-
Published: Monday, 17 April 2017 17:34
-
Written by Guru Advisor
HVM stands for Hardware Virtual Machine and defines a type of virtualization used by Xen which consists in a full emulation of a PC, including processor, video card, disk controller, network interfaces, etc.. HVM virtualization is the most flexible virtualization technique, yet it penalizes performances for every operation must be simulated via software.
- Details
-
Category: Word of the Day
-
Published: Friday, 14 April 2017 17:34
-
Written by Guru Advisor
The Storage Spaces Direct (S2D) technology is a new feature of Windows Server 2016, available only with the Datacenter version. It requires at least 2 nodes with 2 SSDs and 4 additional disks each in order to work. The peculiarity of this system is the capability of using hosts with integrated storage (SATA, SAS or NVMe) instead of external ad-hoc solutions to realize an overall secure, scalable and high performing system. In its broader configuration, S2D can work with 16 hosts and up to 400 drives for a total storage capacity in the order of the Petabyte, with disks hot-add capability. Communication between nodes requires 10GbE network hardware with remote-direct memory access (RDMA).
- Details
-
Category: Word of the Day
-
Published: Thursday, 13 April 2017 17:34
-
Written by Guru Advisor
Resilient File System (ReFS) is the new file system by Microsoft introduced in Windows Server 2012 and 2012 R2 (and 8.1 as a consequence), which finally comes to a stable version in Server 2016. It was born to optimize data management and guarantee integrity and persistence to damages, even in the case of large data sets and regardless of the underlying hardware structure. Key points of ReFS are integrity, availability, scalability and proactive correction of errors.
- Details
-
Category: Word of the Day
-
Published: Wednesday, 12 April 2017 17:34
-
Written by Guru Advisor
A Zombie VM is a virtual machines with issues (subtle, most times) that provoke an anomalous resource usage of the host it runs on, also after being detached. A synonym of Zombie VM is Orphan VM.
- Details
-
Category: Word of the Day
-
Published: Monday, 10 April 2017 17:34
-
Written by Guru Advisor
The term Data Lake comes from the Big Data world and describes a "save everything" approach here each piece of data is stored, be it structured or not. Data Lake represents a large repository composed by data thus collected and easily accessible.
- Details
-
Category: Word of the Day
-
Published: Friday, 07 April 2017 17:34
-
Written by Guru Advisor
The term Rainbow Table identifies a table used in the cryptography sphere for the research of clear ciphering keys. The table is a compromise between running time and the request of resources needed to decrypt keys in hash format, generated by a certain ciphering function. This technique was conceived by Martin Hellman, but only in a theoric way as it would require too many Terabytes of memory to store all possible hashes. Later Philippe Oechslin optimized this concept so that it could be used in practice.
- Details
-
Category: Word of the Day
-
Published: Monday, 30 January 2017 17:34
-
Written by Guru Advisor
HTML5 is a markup language for the creation of Web pages, first published in October 2014. It’s conceived as the successor of HTML4 and as the substitute framework of Adobe Flash. One of the main features is the capability of storing (within the browser’s local cache) a large quantity of data that can be used by Web-based applications also without an Internet connection. HTML5 is more secure, flexible and lighter than Flash.
- Details
-
Category: Word of the Day
-
Published: Monday, 30 January 2017 17:34
-
Written by Guru Advisor
The tem File Descriptor describes a non negative integer value, peculiar of Linux/Unix operating systems, that identifies a certain file, socket or running process (that is making I/O operations) within the system. This ID is generated by the kernel and it's used and ID index in tables of active entities.
- Details
-
Category: Word of the Day
-
Published: Thursday, 26 January 2017 17:34
-
Written by Guru Advisor
XML stands for eXtensible Markup Language and defines a markup language that is based on a specific syntax to define and control the meaning of the elements contained in a text. The main characteristic of XML is creating custom tag, hence the name eXtensible.
XML is also often used to export data in a standard format from a proprietary database.
- Details
-
Category: Word of the Day
-
Published: Tuesday, 24 January 2017 17:34
-
Written by Guru Advisor
The term Ads (Advertising) is a generic term for all advertising communication techniques that are used to promote a certain product. In the IT world it’s commonly found while browsing the Web as banners inside Web pages that capture the attention of the reader.
You can limit or block Ads while browsing by installing an “Ad-blocker”.
- Details
-
Category: Word of the Day
-
Published: Tuesday, 24 January 2017 17:34
-
Written by Guru Advisor
The term Ad-blocker defines a browser component (if talking about Web browsing) which can intercept and block ads within a Web page that can be annoying, hinder the experience and slow the loading because of all those extra ads content.
- Details
-
Category: Word of the Day
-
Published: Monday, 23 January 2017 17:34
-
Written by Guru Advisor
Crontab is a UNIX command that creates a table (or list) of commands that the operating system will execute automatically according to a certain schedule. The crontab command creates a file called Crontab file.
- Details
-
Category: Word of the Day
-
Published: Friday, 20 January 2017 10:00
-
Written by Guru Advisor
The acronym ACL stands for Access Control List and basically defines a table used by an operating system, or a firmware (ie network devices) where access rights to resources are specified for each user. Every object in the system has a specific security attribute which identifies its own ACL and regulates the usage by part of users according to the assigned privileges.
- Details
-
Category: Word of the Day
-
Published: Thursday, 19 January 2017 10:00
-
Written by Guru Advisor
The term Domain Controller (DC) defines a specific role typical of the Windows Server operating system that is assigned to the host that will manage the authentication of users in a domain environment. A DC can be Primary (PDC) or Backup (BDC); the former periodically sends an up-to-date copy of the users database to BDCs (which can be more than one) in order to guarantee uptime if it fails.
- Details
-
Category: Word of the Day
-
Published: Wednesday, 18 January 2017 10:00
-
Written by Guru Advisor
FQDN is the acronym for Fully Qualified Domain Name, which is the part of the URL that univocally identifies the server it’s being contacted across the Internet. The FQDN includes the second-level domain and all related subdomains, which basically is anything is left of the TLD extension (xxxx.example.com, xxx2.example.com etc.).
- Details
-
Category: Word of the Day
-
Published: Tuesday, 17 January 2017 10:06
-
Written by Guru Advisor
The term crawler describes a type of software the visits Web sites available on the Internet and checks content and information with the aim of creating search engines indexes and keeping them up-to-date. One of the particular features of a crawler is being able to visit each single page of a Website by also following any additional external links present.
- Details
-
Category: Word of the Day
-
Published: Wednesday, 04 January 2017 10:00
-
Written by Guru Advisor
The term Custom TLD, or Custom Top Level Domain, indicates those domain names that have been introduced and recognized by the ICANN association since April 2012. The most known TLDs like the historical .com, .net. and .org are now sided by custom domains and from then it’s possible to buy and use extensions such as .car, .home, .hobby and even .organization_name.
- Details
-
Category: Word of the Day
-
Published: Tuesday, 03 January 2017 10:06
-
Written by Lorenzo Bedin
Eye-Fi is the name of a technology used with memory cards to transfer data from the card to the destination device in a wireless manner.
Usually memory cards with Eye-Fi capabilities are used with digital cameras.
- Details
-
Category: Word of the Day
-
Published: Monday, 02 January 2017 10:06
-
Written by Lorenzo Bedin
The term Dynamic DNS, or DDNS, describes a mechanism with which a DNS system is automatically updated as soon as the associated IP address (or domain) is changed.
A classic application of DDNS is when a host with a public IP must be in perfect correspondence with the same domain name.
In order to work, a DDNS requires a client to be installed on the host which owns the interested IP address or, as an alternative, it’s often integrated with the firmware of gateways and routers.