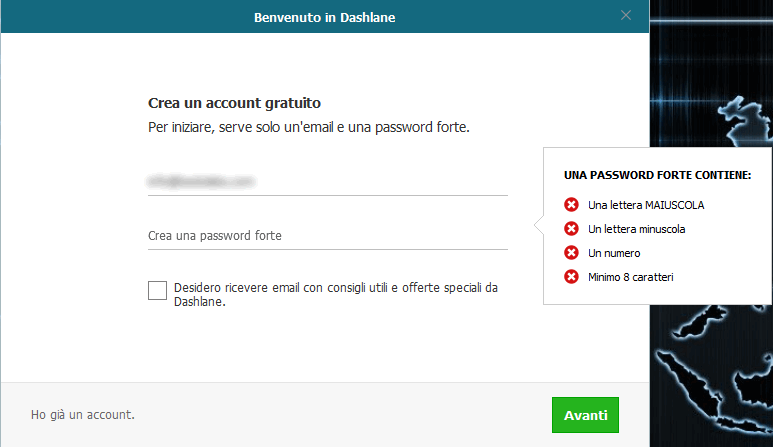
Is there a solution to the hell of a problem about all those passwords you should adopt in your personal and working life? Yes, there is!, and it’s called password manager: let’s see what it is and how it can change your life for the better.
A password manager is a software that has storing and management capabilities in a single, secure place for all your access credentials and protects them by means of a single primary password. The main goal of this kind of software is to guarantee the security of stored data and a structured management (research, update, deletion, etc..).
Unlike manual solutions like spreadsheets or even paper notes, a software like this helps you to maintain an archive through time or with a growing number of information. Moreover, it provides a better security level, simplify adding passwords and include interesting features as the automated generation of secure passwords and advanced research features.
The point of strength of a password manager lies in its centralized nature: you only need to use a primary key in order to protect the entire archive. Of course, the complexity of such key must be quite elevated (capital letters, symbols, numbers, length, etc..) and most platforms offers a two-factor authentication (or a so-called additional key file) system that further strengthen the overall security level. Some software even allows the creation of users with different access permissions, so that a single archive can be used with different visibility levels according to the authorizations assigned to each user, just as in a typical business scenario.
Despite each different product having its own personalized interface, the common idea behind password managers is to offer a dedicated window to each stored identity: not just username and password but also URL (if it’s a resource available on an internal network or on the Internet) and additional notes or related information. This approach broadens the concept of the mere storing of credentials as it provides the user with a protected archive of data.
Some software, like Dashlane, also allows to store scans of IDs, personal information (that can be used with field auto-completion within a browser) and data related to credit cards, banking accounts, etc...
Typologies and security
There are two main families of password managers: those based on an archive file and those that leverage a Cloud platform.
In the former case (ie Enpass or KeePass), the archive is stored in an encrypted file saved locally on the device, be it a computer or mobile, where the program runs on, while in the latter case (ie LastPass) all information is stored into the Cloud and accessed by means of a Web interface or browser’s plugin. It’s quite evident that the archive is always available if on a Cloud-based structure, and that the use of local files is limiting in terms of portability. Some products like 1Password use a combined approach with both a Web access and an offline cache.
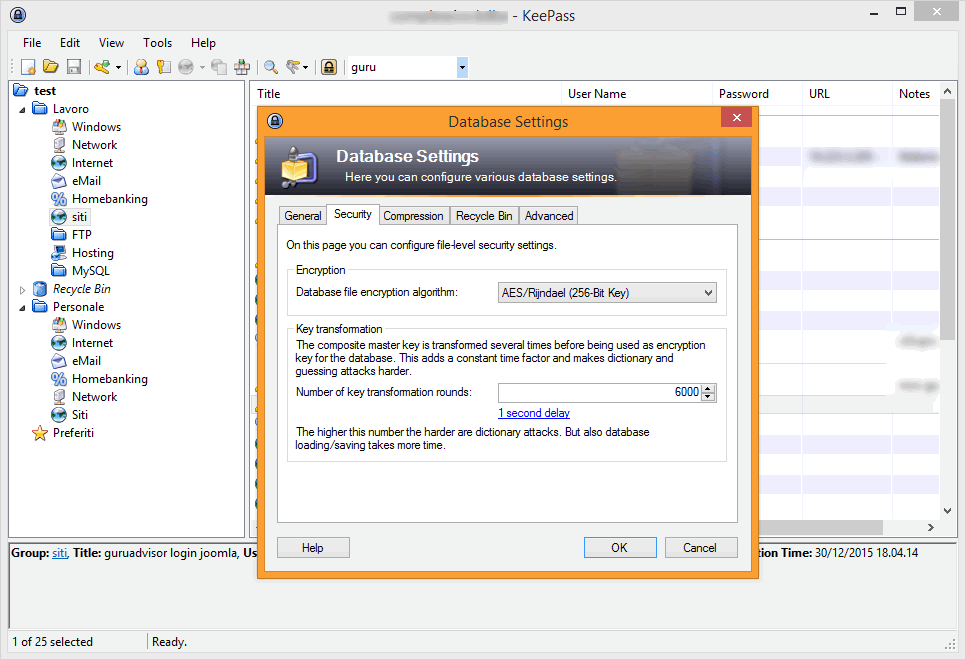
The usage of a centralized archive software might arise some doubts about the effective safety of data as they are saved into the Cloud (and always available across the Internet); more serious products, like KeePass, use a local database that is encrypted with algorithms such as AES-256 and Twofish to protect data and the master password, whose hash is computed with the SHA-256 protocol and is used to encrypt and decrypt the whole archive.
KeePass’ reliability has been the object of a study by an european commission that specifically works within the security field of open source software (EU-FOSSA, or European Free and Open Source Software Auditing project); the results of the auditing of the source code of this famous password manager show that there is no significant security vulnerability.
There are two methods that help to improve the overall security level of credentials: the use of two-factor authentication and the use of a key-file.
Two factor authorization (2FA) is about adding another authentication token to the master password; such token is requested only when accessing from a new device or at each access and it’s sent to the user with an SMS or app.
Using a key-file or a physical token, like and USB drive, might be required in situations where a very high security level is mandatory: in this case, in addition to the master password, you need to add the key file to the password manager software or to insert physically a dedicated USB drive.
Despite the high security standards employed, one of the most used password managers (LastPass) has been violated last spring: Mathias Karlsson, an IT researcher, succeeded in extracting credentials from LastPass by leveraging a vulnerability in the browsers fields auto-completion feature.
Considerations and functionality
As stated before, the concept of password manager has broadened up to include several features the user will find useful, like storing personal data and browser autocompletion.
A basic usage allows to store in an ordinated manner that is also easy to browse of a certain amount of user-password pairs, which can, obviously, be showed and used: most software are multiplatform and available to mobile devices as well.
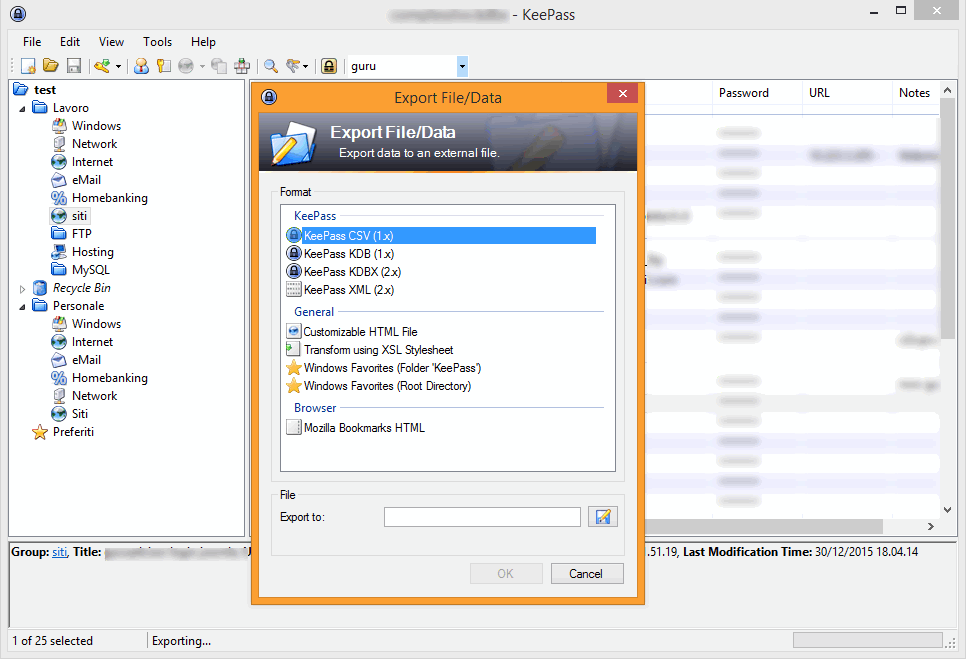
In conclusion, it’s hard to find negative aspects to the use of a password manager that, once the initial impact of those used to use other password management methods, combines security and comfort. Portability is usually good, as the archive can be exported in different formats (CSV, KDB, XML, etc..).