In the previous issues of GURU advisor we have dedicated article and in-depth analysis, like the one on the April 2016 issue, to the phenomenon of crypto-lockers. This plague isn’t showing any sign of slowing down and, if on one hand we have some good news (like the release of the code to decrypt data ciphered by TeslaCrypt), on the other hand new threats arise each week. For instance RAA, developed with JavaScripts and distributed via email as attached .doc file. Despite making it unharmful by disabling the Windows Script Host feature (and, subsequently, the execution of scripts), in practice RAA is another threats to your data. In this article we’d like to widen our knowledge by talking about specific tools to fight ransomware.
Prevention with backups, data protection, etc, still is the best tool at the disposal of users, of course.
A quick recap
There is a large number of tools we’ve already introduced you, so let’s recap them briefly.
- CryptoPrevent by FoolishIT sets Group Policy that prevent some ransomware from being installed.
- TeslaDecoder by BloodDolly decrypts files hit by TeslaCrypt (up to version 4).
- BitDefender offers a tool against Linux Encoded (a ransomware that hits Linux systems) and a vaccine for CTB-Locker, Locky and TeslaCrypt called BD Antiransomware.
- Malwaresbytes Anti-Ransomware, formerly known as CryptoMonitor, blocks CryptoWall4, CryptoLocker, Tesla, and CTB-Locker, but it’s still in beta phase.
- Third Tier Ransomware Prevention Kit contains a set of Group Policy, filters, whitelist, settings, documents and much more to prevent infections from ransomware.
Once hit by a ransomware, the first fundamental step is to discover which crypto-ransomware is responsible for the attack. To do that, the ID Ransomware service by MalwareHunterTeam is particularly effective. By uploading an infected sample file, it identifies the type of ransomware from a pool of 103 different types available in the database. ID Ransomware doesn’t decrypt any file, it lets you know the exact nature of the ransomware attack.
The toolbox
Emisoft, a software house that deals with anti-malware solutions, released a set of tools useful according to the kind of attack: Emisoft tools can decrypt files hit by a large number of ransomware like Nemucod, DMALocker2, HydraCrypt, DMALocker, CrypBoss, Gomasom, LeChiffre, KeyBTC, Radamant, CryptInfinite, PClock, CryptoDefense, Harasom, Xorist, 777, BadBlock and Apocalypse. Executable files can be downloaded, instructions included, at this address.
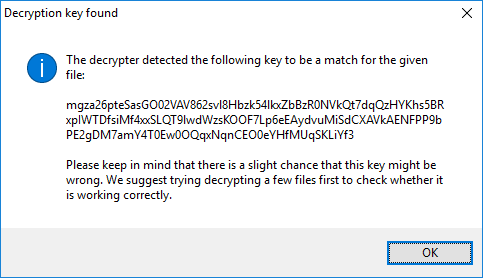
For instance, let’s see how to use the tool against Hydracrypt and UmbreCrypt.
The use is very simple, indeed: drag on the executable file two files (which are either an encrypted file and an unencrypted version of the same file or an encrypted PNG image and whichever PNG image found on the Internet) in order to obtain a decryption key. It could happen that the last bytes of the files don’t get decrypted: in some case all you need to do is open and save the file, in some other you need a dedicated tools, and, unfortunately, in some others, file could remain corrupted.
Moreover, this tool doesn’t delete encrypted files, so be sure to have enough free space available on the disk in order to have both encrypted and decrypted versions.
Hack-petya by Leostone is, as the name suggests, a tool dedicated to decrypt files compromised by the Petya ransomware, a malware that modifies the Master Boot Record (MBR), which is an important sector of the disk that contains instructions about the operating system boot. As a matter of fact, such attack, in addition to prevent files from being accessed, makes the system not usable at all.
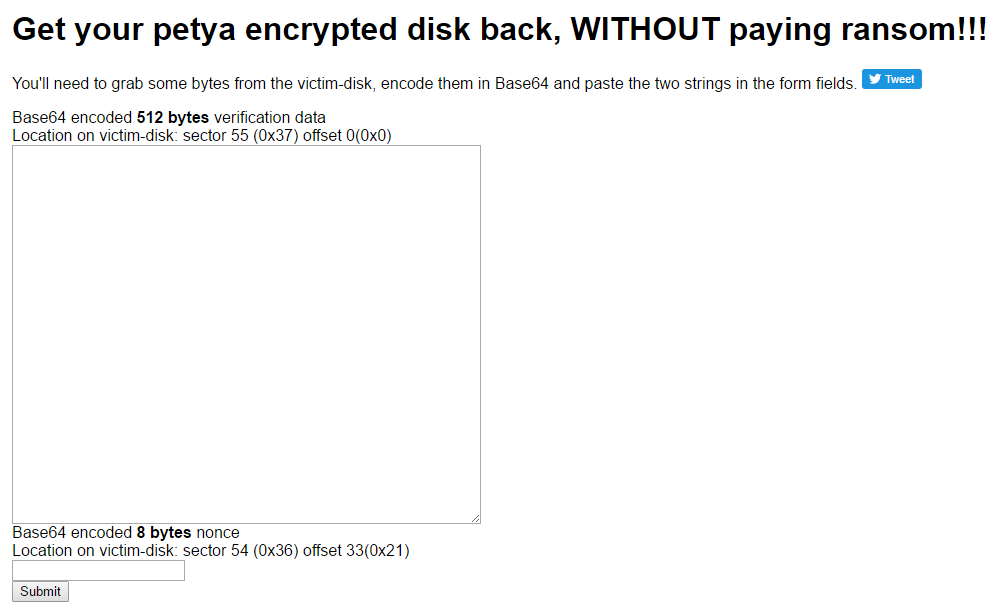
This tool (download it here) asks for two particular files the user has to generate which collect information about the infected disk. Luckily another developer, Fabian Wosar, made a dedicated tool available, which spares the user from this task.
The infected disk must be connected to a Windows computer where Petya Sector Extractor is run, giving back as output two alphanumeric strings (Sector and Nonce) that must be pasted into the online form in order to obtain, in a few seconds, the decryption key. At this point, put back the disk on the original computer, power it on and insert the key in the payment window so that the ransomware can start to decrypt data.
Green Petya is the new version of Petya that includes the Mischa ransomware. Should Petya fail to install (eg, there are controls on access as Administrator), Mischa makes its appearance: it doesn’t require any administrative privilege and encrypts the whole disk. There are no efficient tools available yet, but we’d like to signal the peyta_green tool by the developer rhasherezade, which however has to be compiled from the binary source code, an operation not for all.
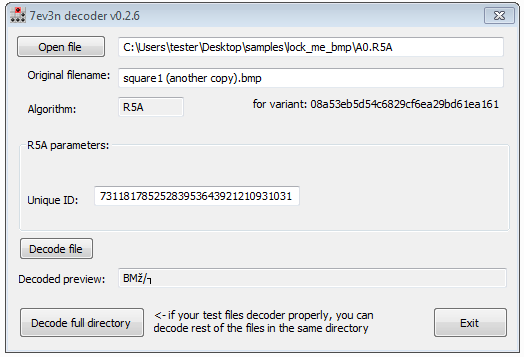
The same developer offers other tools to decrypt files hit by the 7ev3n ransomware, by its evoluted 7ev3n-Hone$t version and by DMA Locker, albeit only for version before 3.0 (download available, respectively, here and here).
The RansomwareRemovalKit kit by Jadacyrus is a set of resources (the extracted .zip file is almost 300MB) for the decryption of files infected by several ransomware: BitCryptor, CoinVault, CryptoLocker, CryptoDefense, Locker, TeslaCrypt, TorrentLocker and many ore.
Unfortunately it hasn’t been updated in months and some information, for instance about Locker and CryptoLocker, is obsolete, however it’s a great starting point for infections from older crypto-ransomware.
Operation Global III is a ransomware that is getting old but still circulates: OG3 Patcher is the tool to remove it; the download package includes additional information and a video-guide on how to use it. Once downloaded, click on the ‘Patch’ button and wait for a confirmation of the proper outcome. The downside of this tool is that is decrypts files one by one, thus resulting in a great amount of work if there are lots of files to decrypt.
Jigsaw appeared last spring and it’s a feared ransomware: by drawing inspiration from the horror movie saga “Saw” -where victims are asked to overcome cruel trials in order to survive- Jigsaw, in addition to a ransom request, adss the deletion of files from the hard disk, with the number of deleted files growing with time and with each reboot of the infected machine. Luckily there’s a dedicated tool that you can download here.

The software by the French Talos (which is part of Cisco’s CSI - Collective Security Intelligence) allows the decryption of files hit by all versions of TeslaCrypt and AlphaCrypt, a ransomware of the same kin of TeslaCrypt.
The use is easy in this case, too: you need to copy the key.dat file, which is generated by the ransomware in the %appdata% directory, and run the executable file. Naturally you can decrypt a certain file or directory or all encrypted files, including those on a network share.
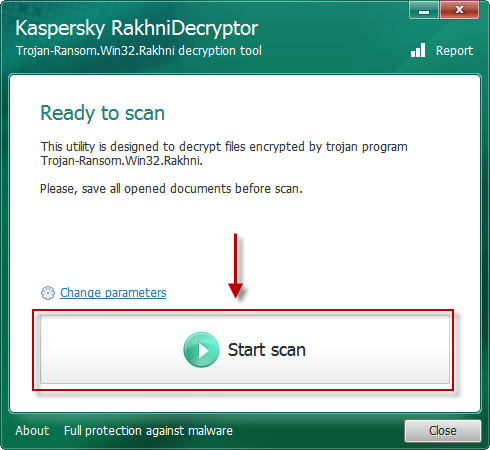
Kaspersky needs no introduction, and it offers a series of tools available at this address: each one include a guide with detailed information about ransomware, or malware, that eliminate. For instance we have RannohDecryptor, which can decrypt files hit by CryptXXX (a TeslaCrypt variant) and ciphered with the .crypt extension, and RakhniDecryptor which decrypts files hit by Cryptokluchen. With regards to these two tools, Kaspersky offers an online service called Noransom, a Website that offers executable files and instructions to decrypt files hits by Rakhni, Agent.iih, Aura, Autoit, Pletor, Rotor, Lamer, Lortok, Cryptokluchen, Democry, Bitman (TeslaCrypt) v3 and v4, Rannoh, AutoIt, Fury, Crybola, Cryakl and CoinVault.
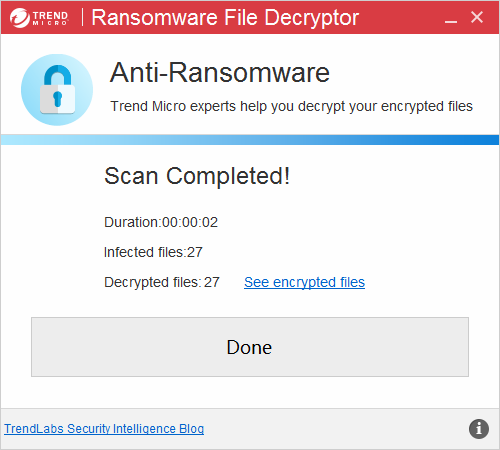
Trend Micro offers some free tools too, at this address. In particular, we’d like to cite Trend Micro Crypto-Ransomware File Decryptor, effective against CryptXXX (note: for version 3 of CryptXXX, a third-party tool is needed for the complete recovery of files as the results of this tool are only partial), TeslaCrypt, SNSLocker and AutoLocky.
Similarly, Trend Micro Lock Screen Ransomware is effective against Lock Screen ransomware which blocks the screen with an image containing a ransom request, thus preventing users from using their computers.
In both cases detailed instructions with screenshots are included.
Expanding our analysis to reports and documentation, BleepingComputer is a valid point of reference in the malware and IT threats world: it offers a large array of specific tools, in depth article and a weekly overview on the general state of ransomware. The forum is particularly active, for instance it offers a tool for the GhostCrypt ransomware.
Lastly we have Ransomware Overview, a very useful document available on Google Documents created and distributed with Creative Commons license by Mosh. This document contains information about the various ransomware such as encrypted file extensions and decrypting tools, if available. It can be downloaded as .xlsx or .ods file for local consultation.
As we have seen together, there is a number of solutions to cure computers and disks infected by ransomware, but the number of situations without a solution is even greater. For instance there is no tool for Locky, which is recognized as the #1 issue by security experts.
The advice we’ve given you still holds, like adopting proper group policies, scheduled and protection of regular and tested backups, constant and immediate OS and program updates, and using file systems with an integrated snapshot system (like ZFS, as described here).
If you know tools or tricks we haven’t covered and you’d like to share them with us, write us at info [at] guruadvisor.net!


























