How to backup PCs/servers
In order to prevent ransomware to infect your backups you can’t store them on a regular network share or on an USB disk: you must choose a local, not accessible backup or a Cloud backup like 1Backup or a similar service.
In this issue of GURU advisor we’ll explain how to leverage snapshots of the ZFS file system with FreeNAS and be protected against ransomware.
The ideal scenario is where your backup is performed on a separate Nas or server which is not linked to any domain or has reduced privileges (principle of least privileges). In any case no clients in use should directly access backups without a password (which also must not be stored). If you are already using a backup software on clients, check if you can add a pre/post backup command to use to add and the disconnect shares immediately after use.
Software that performs a Cloud backup now offer a natural protection against ransomware: be careful that data is not stored on a space that is also locally available such as the Dropbox or the Google Drive folders, because ransomware could also encrypt such folders.
How to protect: specific tools
Some specific tools for the protection against ransomware are available. The overall panorama has changed compared to the one of our last article: CryptoRadar is no longer available and its site seems to be closed, and CryptoMonitor has been acquired by MalwareBytes. This tool can be downloaded at the MalwareBytes’ forum, but it’s still considered in beta phase, not to be used in production environments.
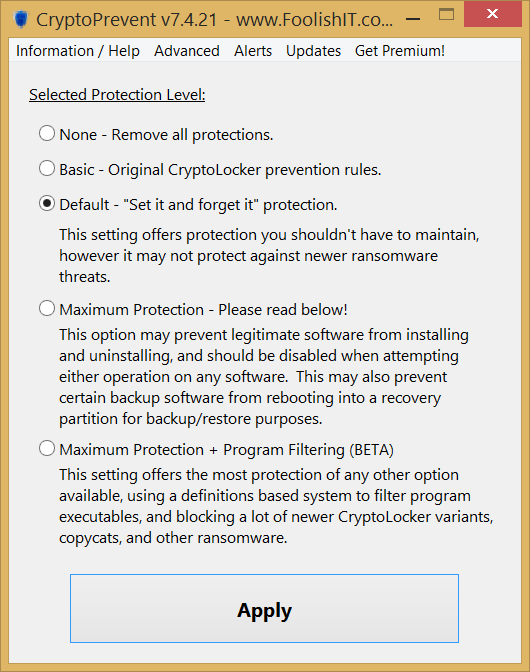
Another interesting tool, free also for professional use and paid if the automatic update feature is required, is CryptoPrevent by FoolishIT.
This simple tool for Windows applies a number of policies that prevent the installation of the most common ransomware. It’s not a lot, but it’s still another layer of protection that can limit potential damages.
Ransomware Prevention Kit by Third Tier is similar, but it's not a software, just a collection of several documents and Group Policies, WMI Filters and Software Restriction Policies for PCs and to Active Directory environments to enhance protection. This kit is not free but donationware, a small donation is required in order to receive a link to a shared folder on Onedrive which is always updated.
Continues: tools and technologies of the main security firms.